Finally, some time for penetration testing tutorials again! Today I will show you that obtaining domain credentials through a printer with Netcat is easy!
Printers are sometimes overlooked when looking into pentesting because what should you do with access to a printer? A lot, actually.
Many business-grade printers are connected to the company’s domain through LDAP. LDAP requires domain credentials to authenticate with the Domain Controller. Now, in most cases, you will probably not get an administrator account through this exploit (but you might as well get one!), but you will at least get a domain account you can work with.
Often times printer passwords are just left on default. Somebody orders a printer, connects it to the network, and maybe enters LDAP credentials, but that’s about it because why would somebody hack a printer, right?
So the first thing we need to do after figuring out the printer model is going to google and search for: “Printer Name” + default password or “Printer Name” + manual and try to find the default password for that specific model (try 0000 or 1111 initially).
Alternatively, you can use the praedasploit exploits on https://github.com/MooseDojo/praedasploit
Throughout my career, I actually came across a lot of printers that were left on default logins.
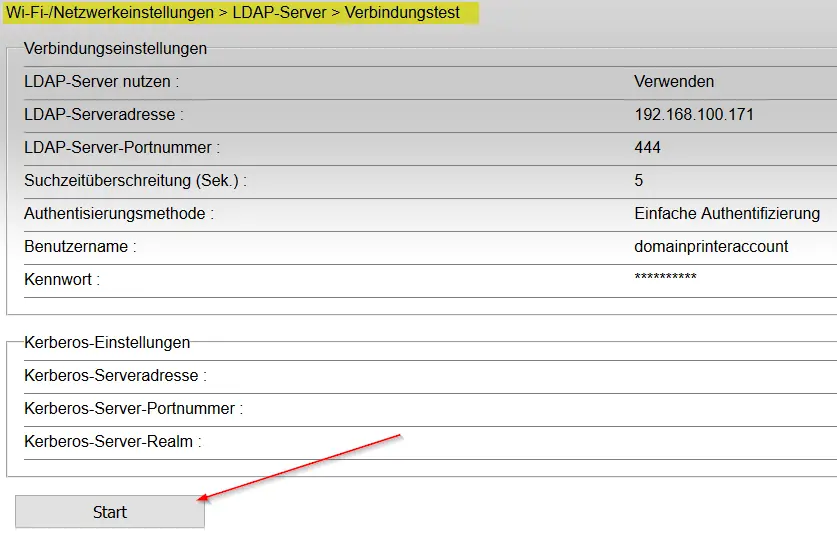
Pointing the printer to our Kali machine
After gaining access to the management console of the printer, we want to navigate to the LDAP settings and point the printer to our Kali machine as the LDAP server.
(Excuse the German language on my printer, but you get the point)
Starting a Netcat listener on our Kali VM
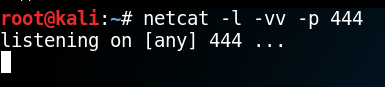
Now we need to start a Netcat listener on port 444 on our Kali VM.
netcat -l -vv -p 444Now we can either wait for someone to Scan a document and for the printer to try to authenticate with our VM, or we can have a look if our printer has the option to test the LDAP connection.
Now, if you look back on your Kali VM, you can see that something happened.
The printer tried to authenticate with your VM and posted the user account as well as the password to the console.
Now you have access to the domain; in rare but likely cases, you will grab a lazy domain admin’s password through this.