Welcome to a new series of tutorials going in the direction of cloud architecture and specifically to AWS with pfSense. In this day and age, a lot of companies don’t want in-house hardware anymore, as the cost of providing a climatized server room and buying physical hardware can get quite high.
Here is where AWS, Amazon Web Services comes into play. You can set up a virtual server in no time and connect it to your internal network through a site to site VPN tunnel.
Did I say in no time? This is, of course, not including the hours and hours of research on how to set the whole thing up. Here I want to give you a little guidance and share with you what I learned along the way and keep you from searching the same solutions I needed to find to solve certain problems.
This is the first part of the whole thing, covering nothing more than the actual Concept of what we want to achieve here.
As mentioned earlier, the lot of small businesses and startups don’t want that server room on their premises, they need the space for motivated employees.
But we still need some kind of Domain authentication, we don’t want users handling their credentials themselves and give everyone local admin rights. We can achieve all this without on-premise servers.
And we achieve this in combination with the mighty open source firewall we all love: pfSense.
Important disclaimer:
I will not teach you how to use AWS or create a VPC or anything the like. As I mentioned in the previous article, there are excellent FREE courses from Linux Academy on the basics of AWS, going through every single step on setting up an AWS VPC and explaining every little detail you need to know to get started. So please, do yourself a favor and go through those courses before trying to achieve anything with AWS, because without this basic knowledge, you WILL fail.
Start with this: AWS Concepts
Continue with this: AWS Essentials
Now without further boring you, let’s get started.
The Concept
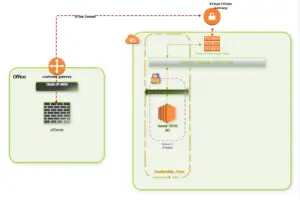
Our basic concept is fairly easy. We want to establish a connection between our local network and our AWS VPC. In this tutorial, I assume you went through the initial process of setting up a default VPC by following the Linux Academy Courses. So you have your VPC, Internet Gateway and NACL rules in place.
What do we want to achieve?
- A secure VPN tunnel between our local network and our AWS VPC
- Installing a Windows Server 2016 as an EC2 instance on our VPC
- Use the Windows Server 2016 as a Domain Controller for our internal network
Sounds easy enough, right?
We will go through each of the steps to achieve this goal, starting with setting up Route53 DYNDNS in Part 2 of this series.
If you are in the same situation and want to learn how to utilize AWS to the fullest, stay tuned and follow along, so we can explore the true potential of Amazon Web Services together.
- Firewall Micro Appliance With 4x Gbe Intel Lan Ports for PFSense
- Firewall Micro Appliance with 2x Gbe Intel LAN Ports for PFSense Barebone
- Firewall micro appliance with 4x Gigabit Intel LAN Ports for pfSense with 4GB RAM / 16GB mSATA
- Firewall micro appliance with 2x Gigabit Intel LAN Ports for pfSense with 2GB RAM / 16GB mSATA
*Some of these links may be affiliate links, meaning if you click and purchase something,
I may receive a small commission at no additional cost to you. I only recommend companies and products I personally use,
and any commissions help to pay for content creation. Thanks!