In this Burp Suite Tutorial you will learn everything you need to know to get started in Web Application Security Testing. Burp Suite is arguably one of the most popular tools when it comes to Penetration Testing, or specifically Web Application Testing. Grab a cup of coffee, you are in for a ride!

Burp Suite
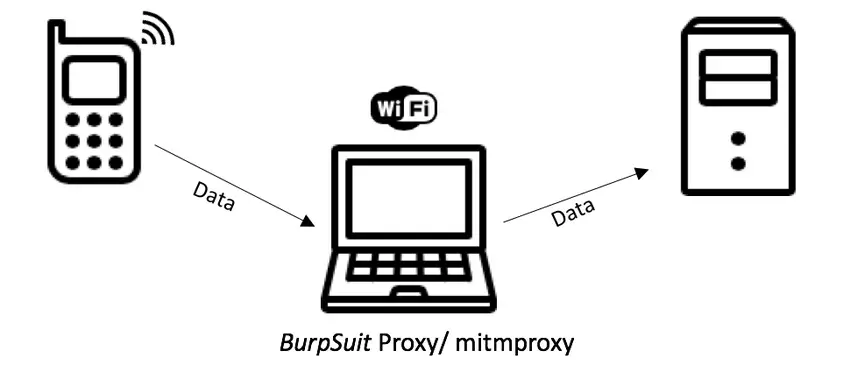
Burp Suite is a collection of multiple tools bundled into a single suite. One of the main features of Burp Suite is the HTTP proxy which sits between the browser and the internet (website) to forward traffic in either direction with the ability to decrypt and read the HTTPS traffic using its SSL certificate, just like a man-in-the-middle attack on ourselves. During the forwarding of traffic, it records, intercepts, replays, and analyzes it while allowing you to manipulate requests and responses from and to the web server.
Other than this, it can be extended with the third-party extensions where you can develop and integrate your own or other’s extension written in Java, Ruby, or Python to automate the testing and the attacks.
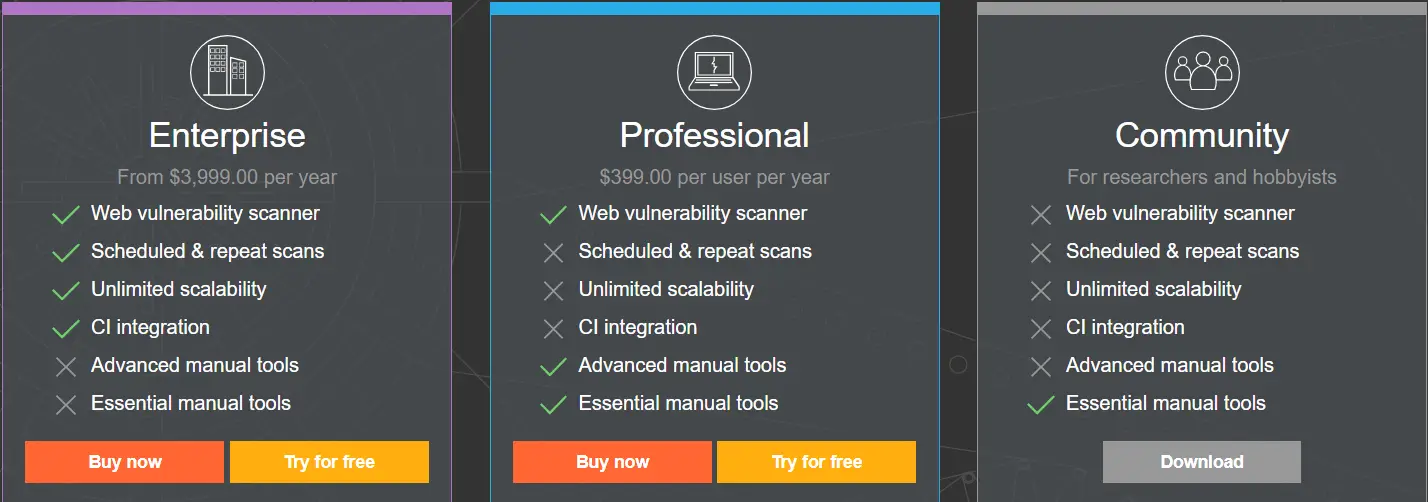
Burp Suite is a Java executable file which makes it supportable on all popular platforms. It comes in three editions from which you can choose from:
- BurpSuite Enterprise
- BurpSuite Professional
- BurpSuite Community
More details regarding the differences between the versions can be found here. The community edition also comes pre-installed with Kali Linux.
The features and their usage In this Burp Suite tutorial I will be covering are the following:
- Main interface
- Configure Outbound SOCKS Proxy
- Intercepting HTTP/S Traffic
- Configuring Intercept
- Configuring the Target Scope
- Searching for a specific term
- Using the Spider
- Using the Repeater
- Using the Intruder
- Passive Scanning
- Active Scanning
- Utilizing Sequencer
- Decoder
- Comparer
- Using the Third Party Extension
- Exporting the Results
- Saving the Burp Session
Main Interface
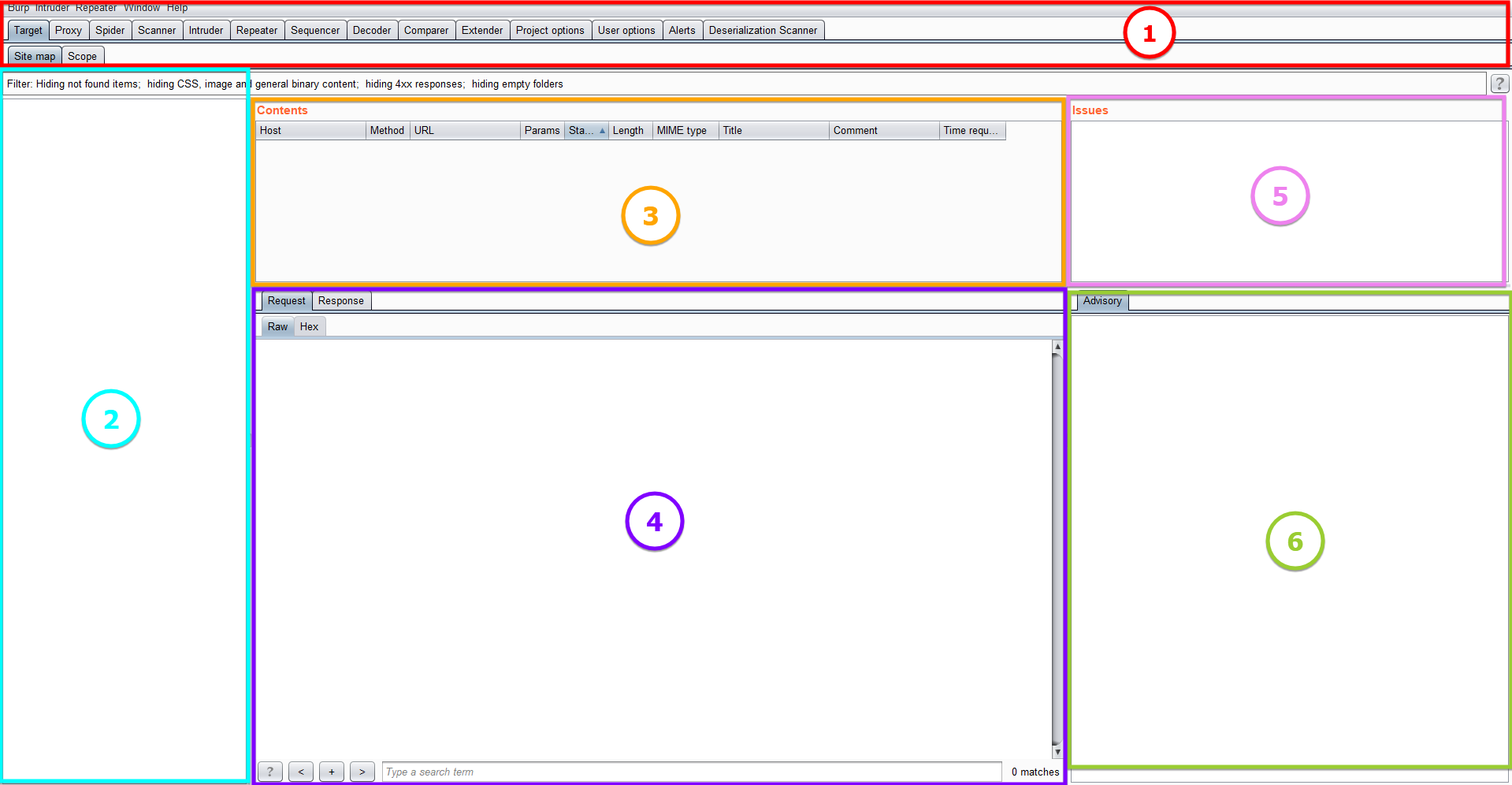
The main interface of Burp Suite which you will get right after starting the application is divided into six sections and multiple panels to work with:
- Tool & Options Tabs – Select between the options and tools to perform different types of operations according to the situation.
- Sitemap View – Displays the sitemap which gets updated by visiting the websites manually or through spidering the websites using the Burp Proxy.
- Requests Queue – Shows the requests being made to the URLs present in the Sitemap View.
- Request/Response Details – The HTTP requests and responses can be read in detail as a result of this selecting the specific request from the Request Queue.
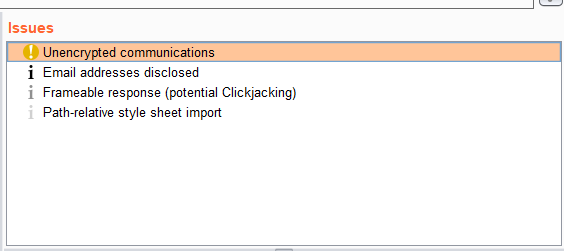
- Issues – The section to view the vulnerability and other application functionality issues regarding the website by selecting the specific website from the Sitemap view.
- Advisory – The section where the Issues are explained in detail how they affect, where they are affecting, their severity, and how to remediate them.
Configure Outbound SOCKS Proxy
Sometimes it is necessary, depending on the scope of your engagement, that you may need to tunnel your Burp Suite proxy traffic through an outbound SOCKS Proxy. It will ensure that all the traffic that passes to the target web application will go through a SOCKS proxy instead of your public IP.
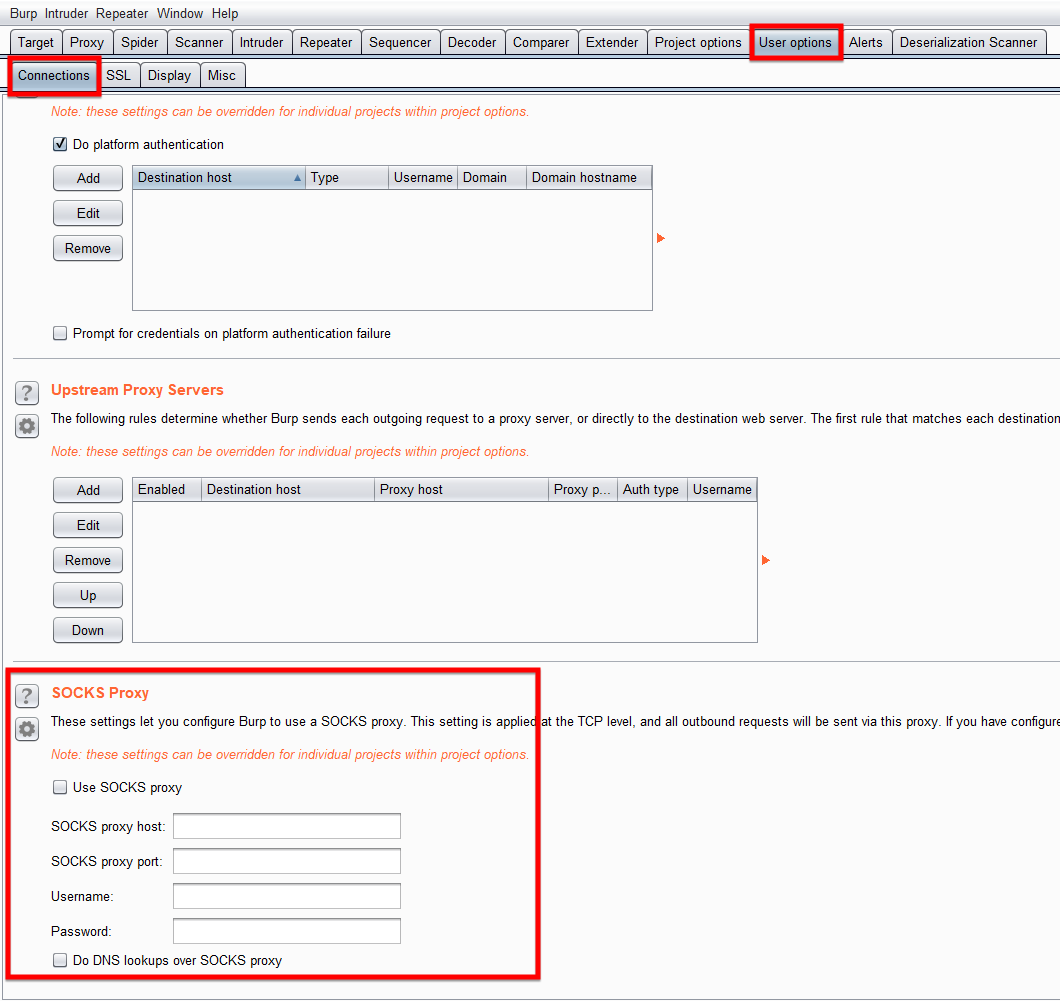
For configuring it, you will need to navigate to the User Options tab located in section 1 as defined before, then choose its sub-tab named Connection, then scroll down to the third section labeled as SOCKS Proxy and enter the details of your SOCKS Proxy there.
Intercepting HTTP/S Traffic
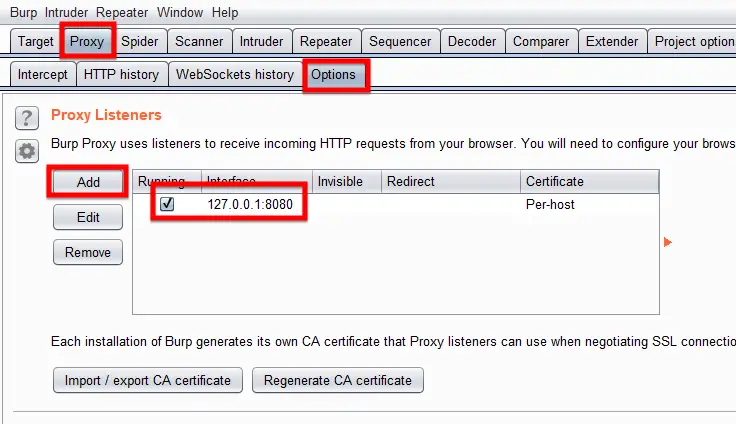
While using the Burp Suite as a proxy, we will need to configure the proxy to make it active and working or else, it will not log and show the URLs and data that is sent or received from the web server. In this Burp Suite tutorial, I will show multiple ways to configure the Burp Proxy in the browser. From section 1, select the Proxy tab then go to the Options tab in the sub row, you will see the Proxy Listener labeled part, enter the proxy details of your local machine to capture its traffic.
Once the proxy configuration is done in Burp Suite, then navigate to your browser and set the proxy configuration there so that the browsers will send the traffic copy to Burp Suite. As the Internet Explorer and Chrome share the same proxy settings, so when you change the setting from either of them, it will reflect in both of them.
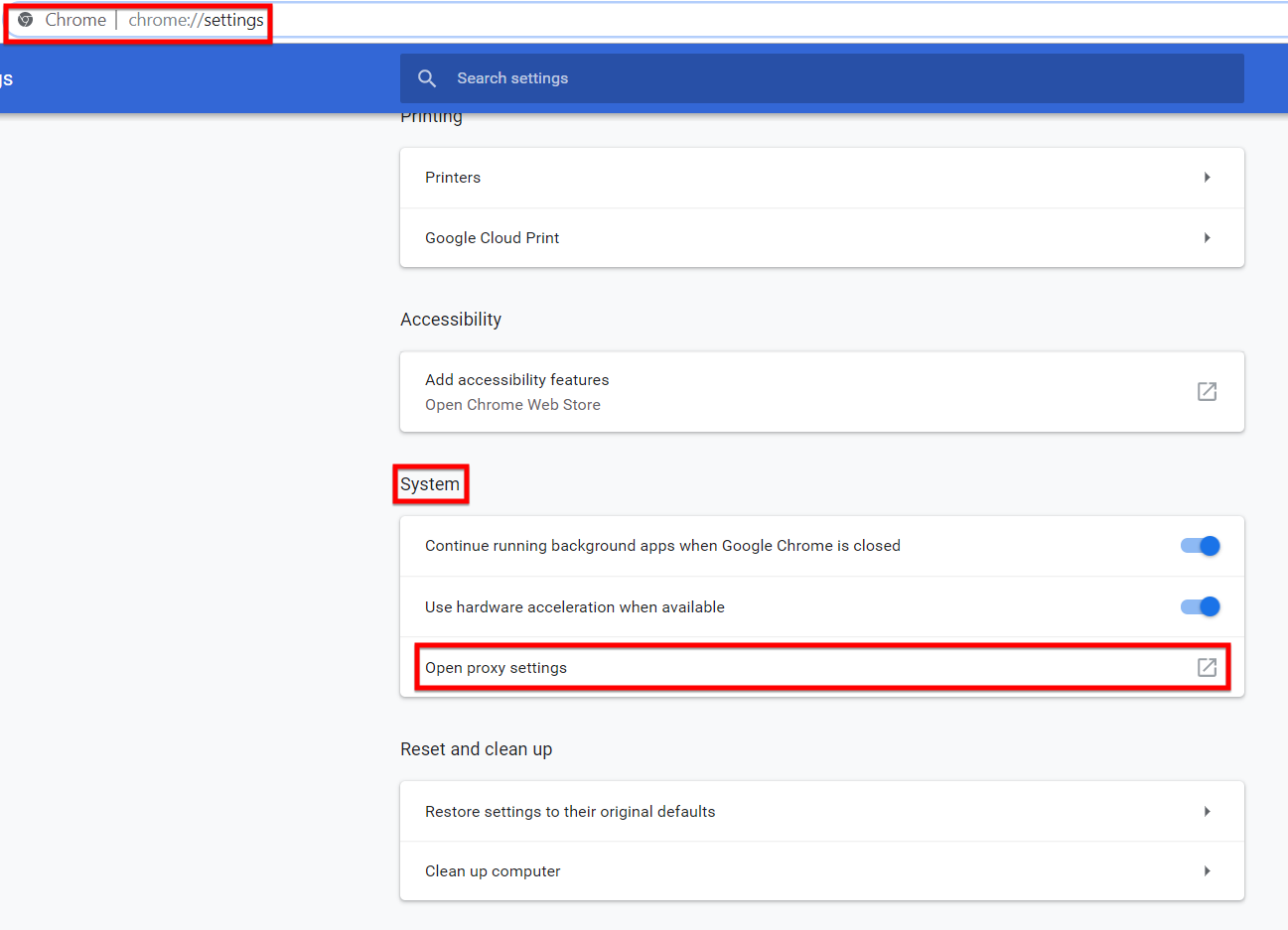
In Chrome, you need to navigate to Settings > Advanced Settings > System > Open Proxy Setting there and enter the same proxy details which you had entered in Burp Suite.
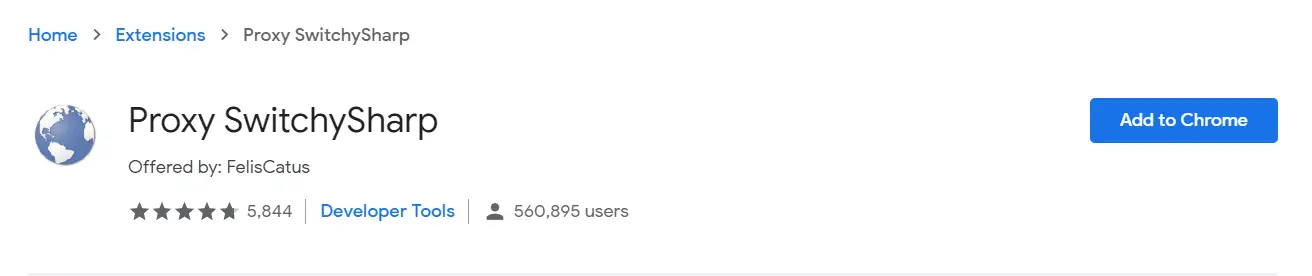
Alternatively, for Chrome, there is even an extension named Proxy SwitchSharp where you once set the proxy and then switch between the proxy or no proxy settings with a single click.
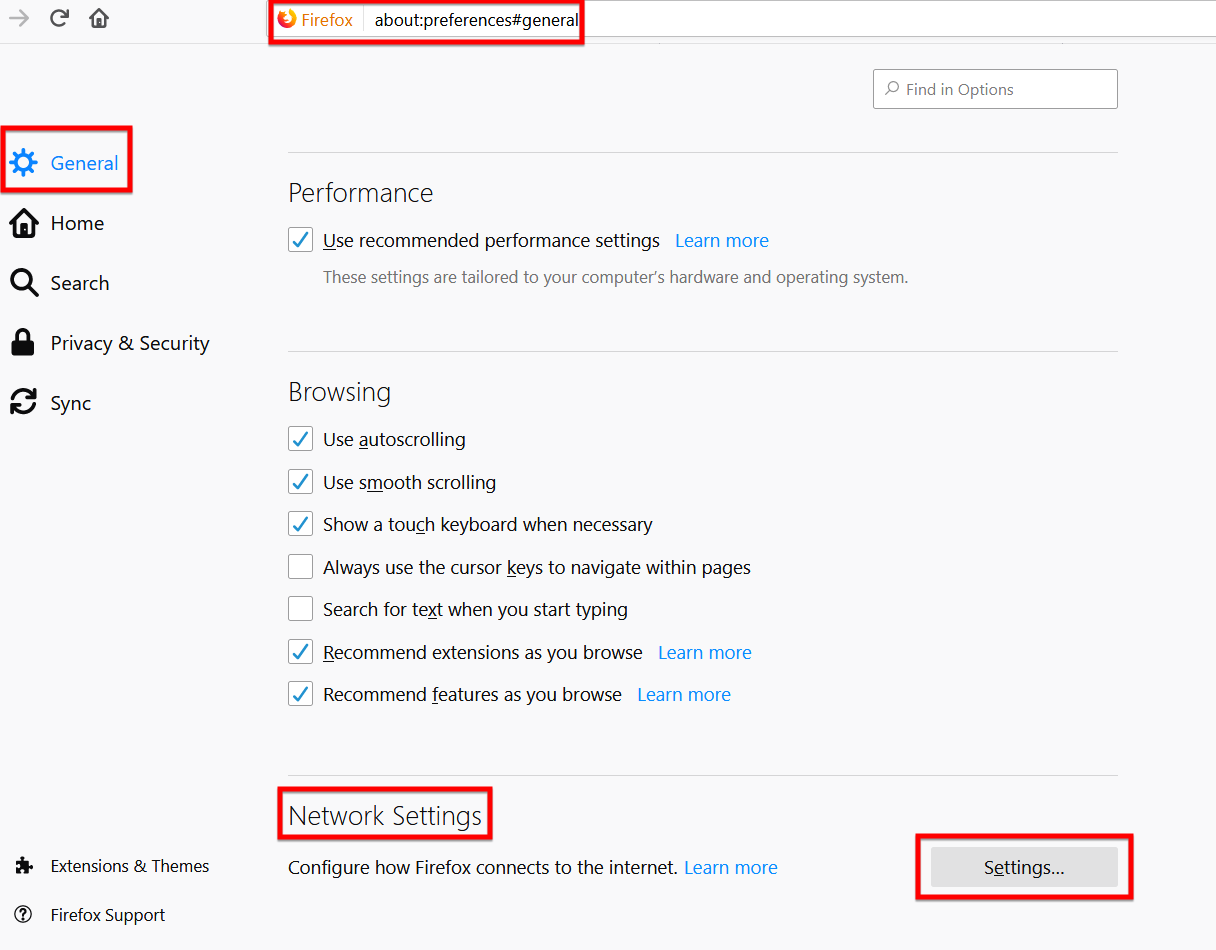
Now we come to the Firefox configuration part, Firefox doesn’t share its proxy with any other application and uses its configuration to use the Proxy. To configure the proxy settings in Firefox, you need to navigate to Options > General > Networks > Settings and enter the same proxy details which you had entered in Burp Suite.
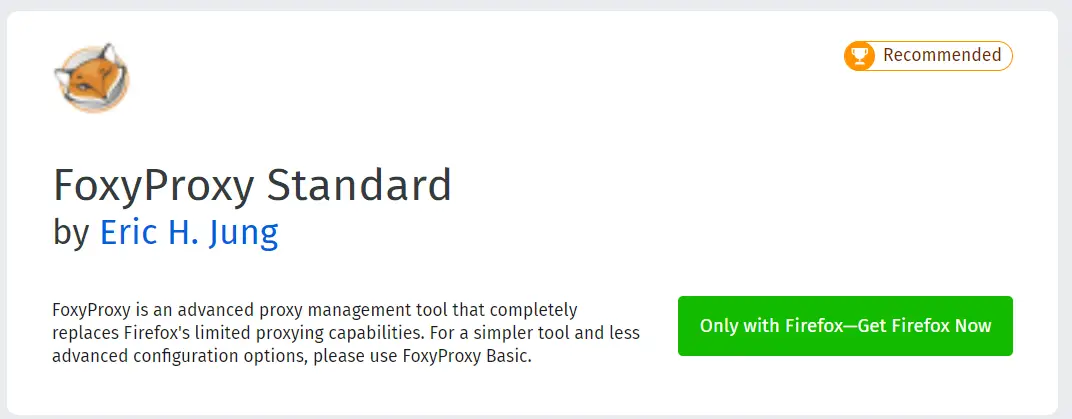
Alternatively, for Firefox, there is even an extension named FoxyProxy where you once set the proxy and then switch between the proxy or no proxy settings with a single click.
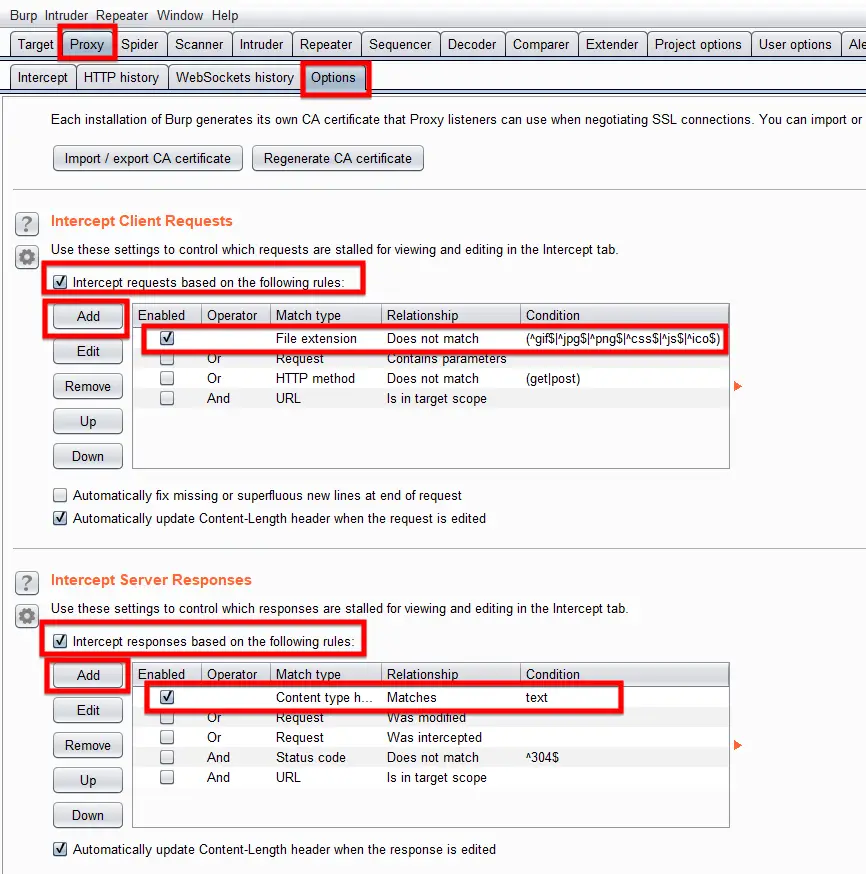
Configuring Intercept
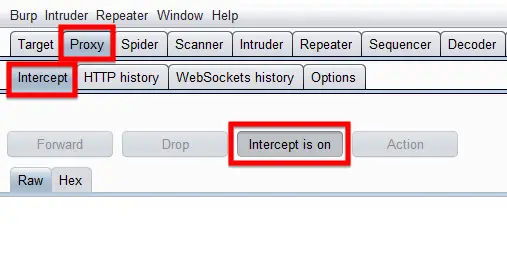
Now comes the proxy intercept feature configuring part of this Burp Suite tutorial. You will need to set and configure it to capture, pass, reject and manipulate the request going to or coming from the web server of the target site. For configuring it, you need to navigate to the Proxy tab, in its sub-tab go to Options and under it go to the 2nd and 3rd section named Intercept Client Request and Intercept Server Request, set their rules accordingly.
I leave them to the default as they are good to go on that. Meanwhile, the Interceptor is used to act as the Man in the Middle can be operated from Proxy > Intercept.
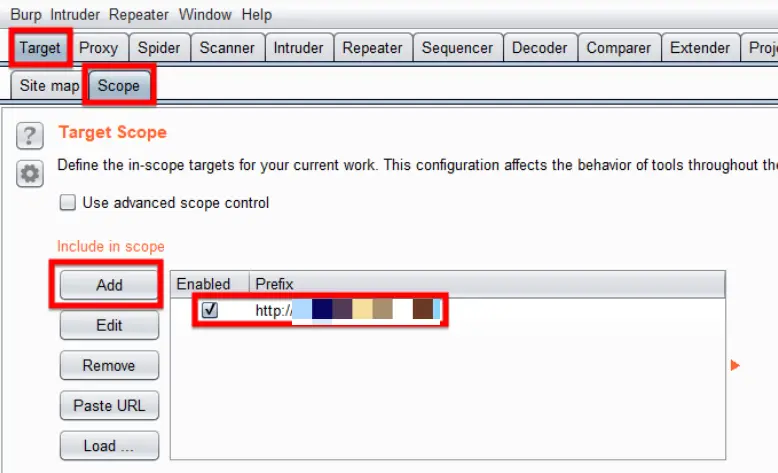
Configuring the Target Scope
Now comes to the part of how Burp Suite will analyze the target application by examining its GETs and POST requests. Before starting any testing, it is recommended and a good practice to set the scope first. By placing a web application in the scope, Burp will only target that specific web application, and whenever you perform any operation against the scope, it will only target the web application(s) that have been set in the scope.
It will ensure that any potentially malicious traffic or payload(s) will not get any web application which you are not authorized to test. Go to the Target tab and choose the Scope sub-tab from there. Click Add there and insert the target URL which you are authorized to test and set your scope.
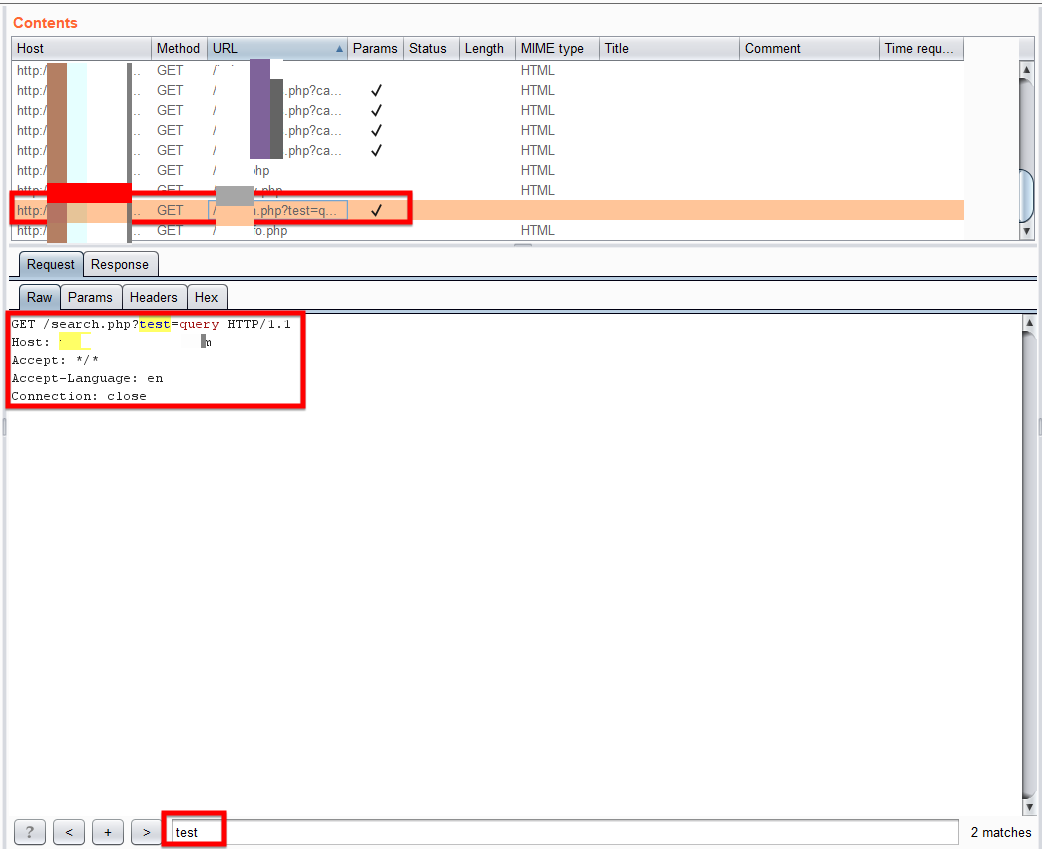
Searching for a specific term
You can rely on Burp Suite to make complicated things easy for you. You can search for any specific term or keyword from the ton of data and information just by typing a keyword. It becomes convenient when you have to look for details like a username or password from the bug results pages. Like I have searched for the “test” parameter which I can further process later.
Searching for a specific term or keyword from the Request or Response data, you need to select a request from the Request Queue and then navigate to either Request tab or Response tab from where you would like to search and enter your desired keyword in the textbox below. It will highlight the text in yellow colour for whatever will match your query keyword.
Using the Spider
Starting with what the spider is? A creepy insect? No. In the web terminology, a spider is a process where a robot goes to the internet and crawls through all of the pages that are available on the target web application. All the pages that the spider will go through on the specific web application will get updated in the Sitemap, which is in section 2 of the main interface.
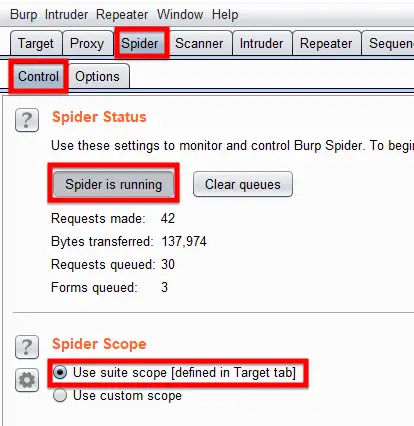
To start the spider on any host, you need to go to Spider tab in Section 1, then in the Control sub-tab, select your scope first as in this Burp Suite tutorial I have defined the suite scope that is actually the scope which I have previously set in the Burp Suite and then hit the Spider running button to run it.
Using the Repeater
The Repeater tab is another one of the most useful features in Burp Suite. I use it hundreds of times during a penetration test. It is used to manipulate any part of the HTTP request including its header and to watch the behaviour of the data which comes back from the server.
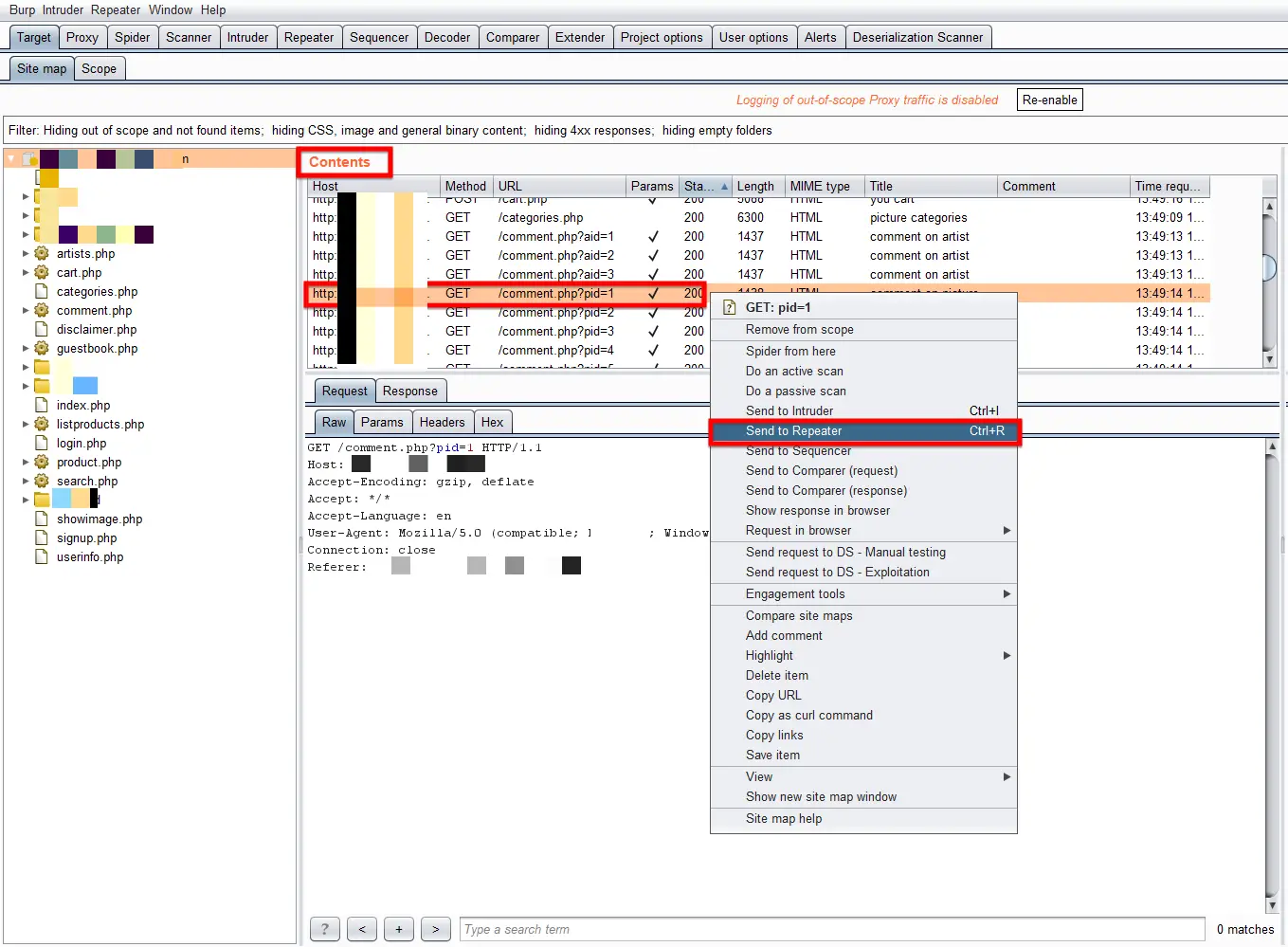
To send and process any request in the Repeater, you need to select and right click on any of the requests from the Request queue and select “Send to Repeater”. Alternatively, there is also a shortcut key that is Control + R to perform this task.
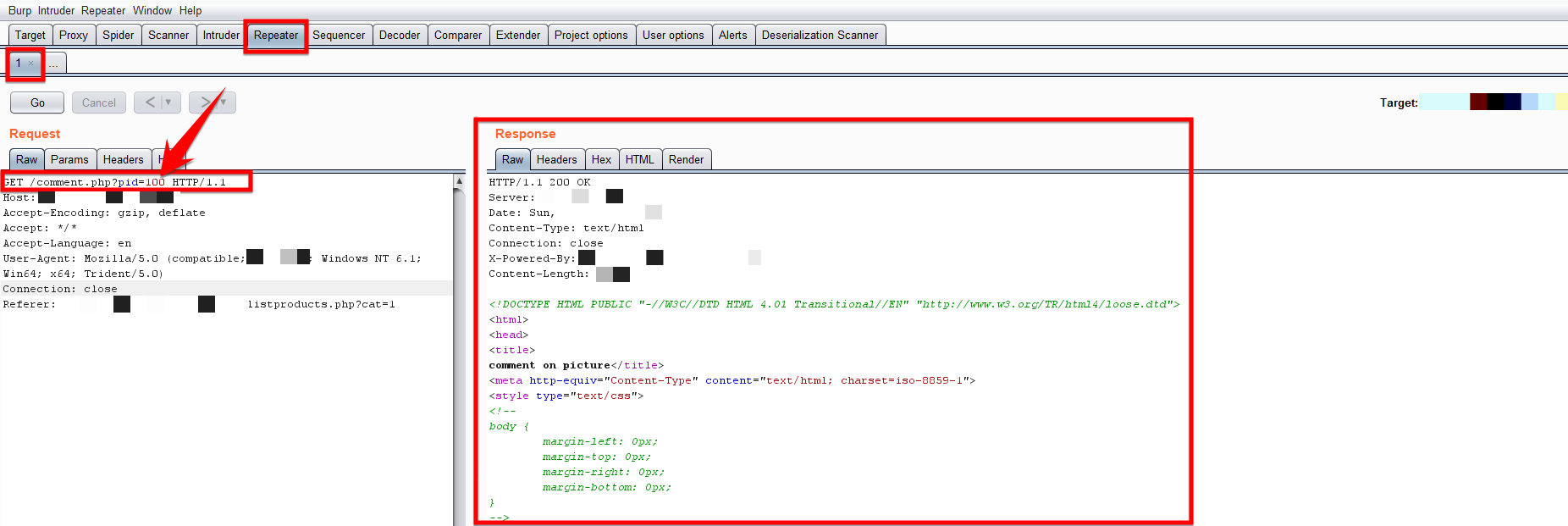
Next click on to the “Repeater” tab and make your desired change in the HTTP request, in this Burp Suite tutorial I have made the changes in the value of pid parameter from 1 to 100 and I hit the Go button and then you can observe the changes in the response from the web application server according to your request which you manipulated.
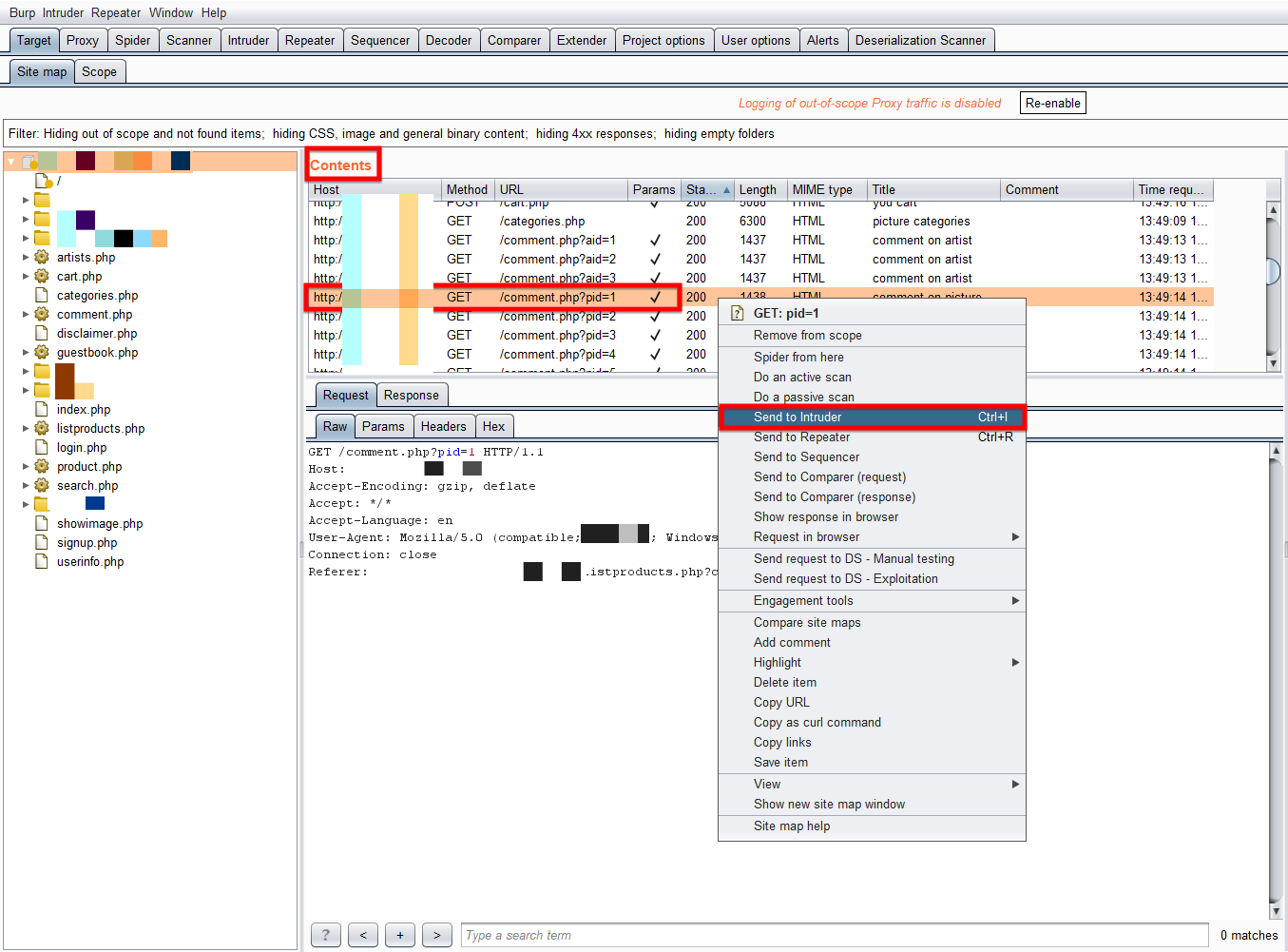
Using the Intruder
The Intruder comes into play when you perform automated testing instead of the manual one. The Burp Intruder is a powerful way to perform automated or semi-targeted fuzzing. You can target it against one or multiple parameters in the HTTP request at the same time.
To send and process any request in the Intruder, you need to select and right click on any of the requests from the Request queue and select “Send to Intruder”. Alternatively, there is also a shortcut key that is Control + I to perform this task.
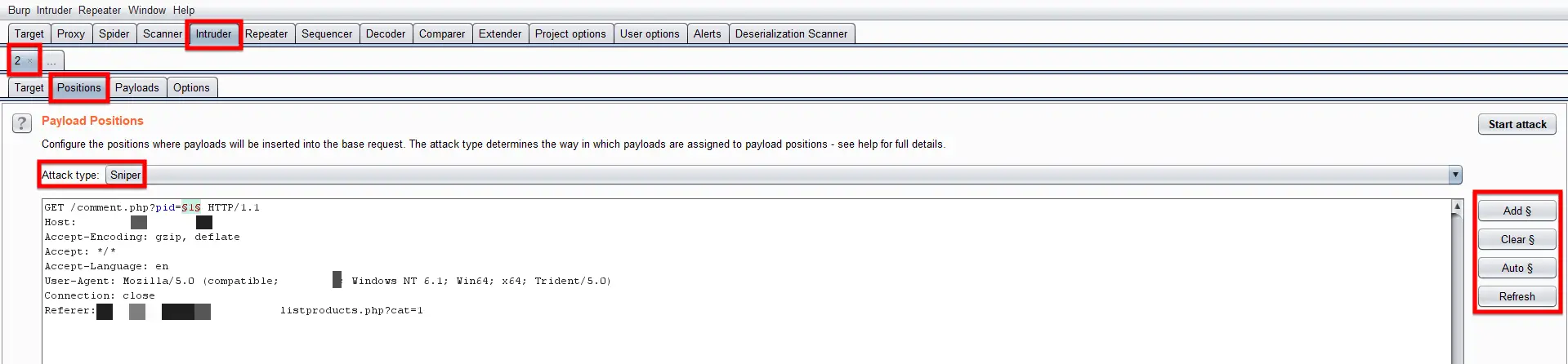
Now go to the Intruder tab and select the name of the current Intruder instance, then click on the Positions sub-tab. You will see the payload input position already been highlighted by the Burp Suite. You can choose your own choice of position or any position suggested by the Burp Suite. In this Burp Suite tutorial, I have gone along with the Burp Suite suggested position.
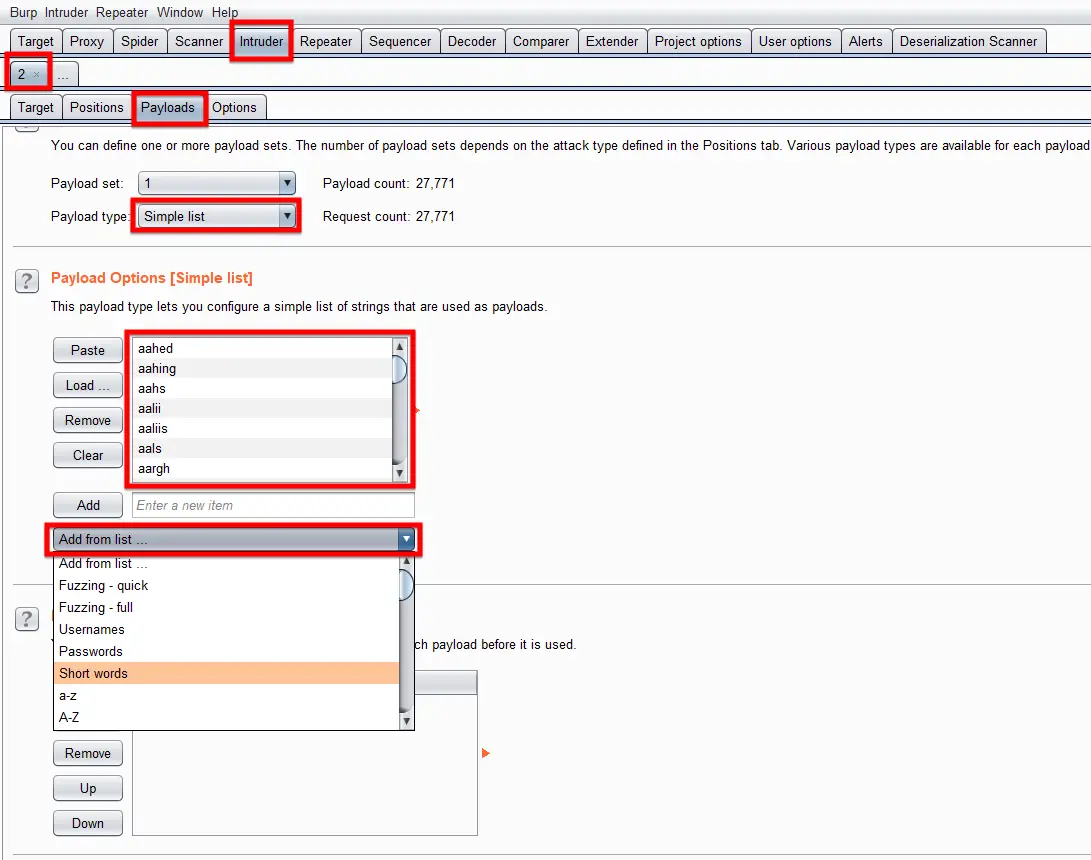
Now head over the Payloads sub-tab and choose the type of payload you want to target against the specific position and click the “Start attack” button. It will push all the payloads against that specific input parameter and shows the results in detail.
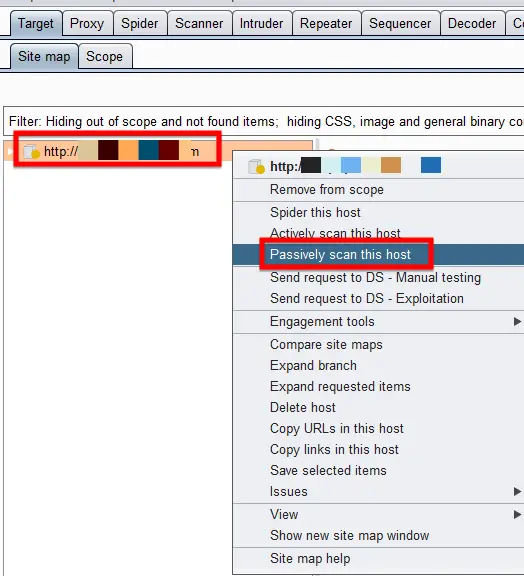
Passive Scanning
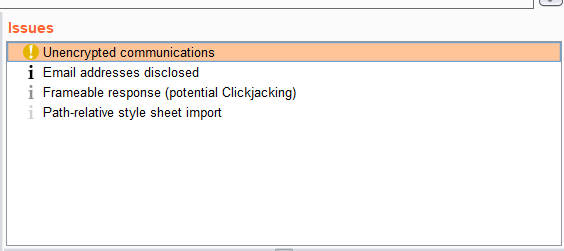
Whenever you go to the browser and visit some pages of the target web application the Burp Suite passively goes into the details of those web pages and analyzes them for the security and other issues and report them in the Issues section which is number 5 on the main interface.
You can passively scan a host, by selecting your desired host from the sitemap and right click on it, then select “Passively scan this host”. It never sends any request to the web server, instead it only analyzes the data that has already been sent by the user while browsing the particular web application.
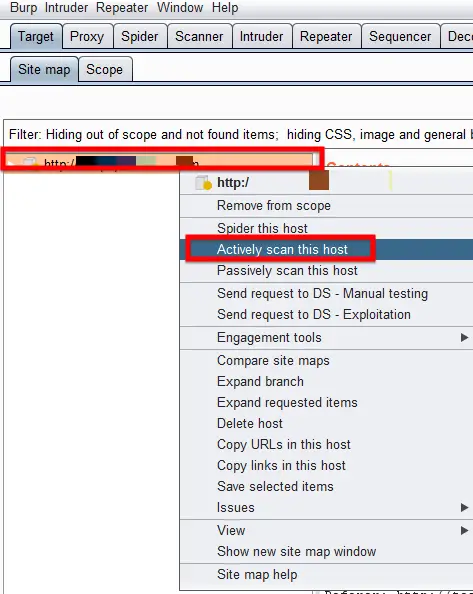
Active Scanning
In active scanning, Burp Suite goes over to the target web application and analyzes and explores it more actively and in greater detail and analyzes it for security and other issues and reports them in the Issues section which is number 5 on the main interface.
You can actively scan a host, by selecting your desired host from the sitemap and right click on it, then select “Actively scan this host”. It sends different types of requests to the web server and creates and analyzes the that it got from the particular web application.
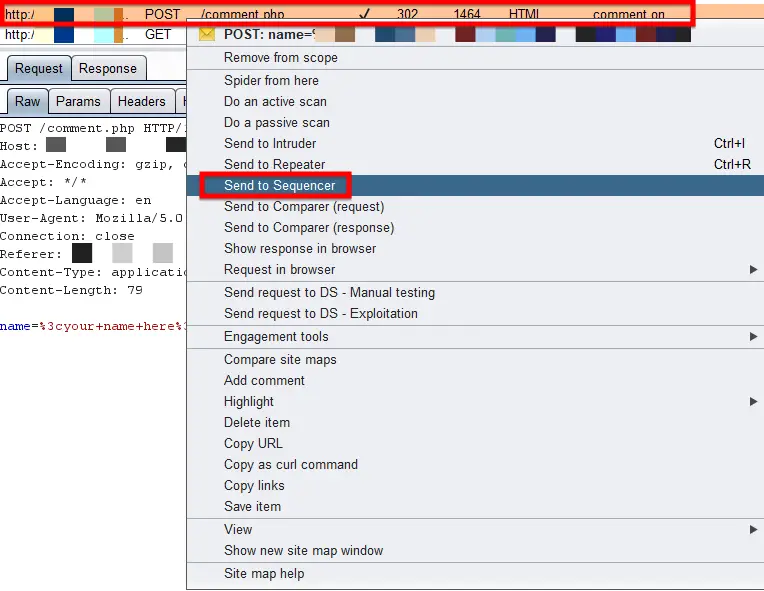
Utilizing Sequencer
The function of the Sequencer is to check the level of randomness in session tokens provided by the web server. It performs various types of advanced tests to figure it out. In most cases, the session tokens are used to provide authentication for a user so they should not get compromised. The web server must use a high degree of randomness for session tokens, so an adversary can not guess it.
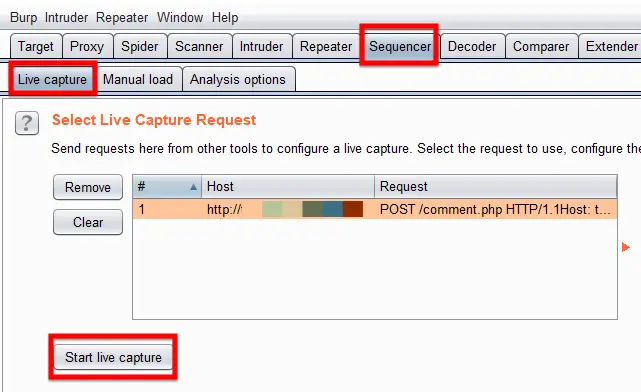
You can perform this test by selecting any request from the Request Queue and right click on it and choose “Send to Sequence”.
Move on to the Sequencer tab, then under the Live Capture sub-tab, hit the “Start Live Capture” button.
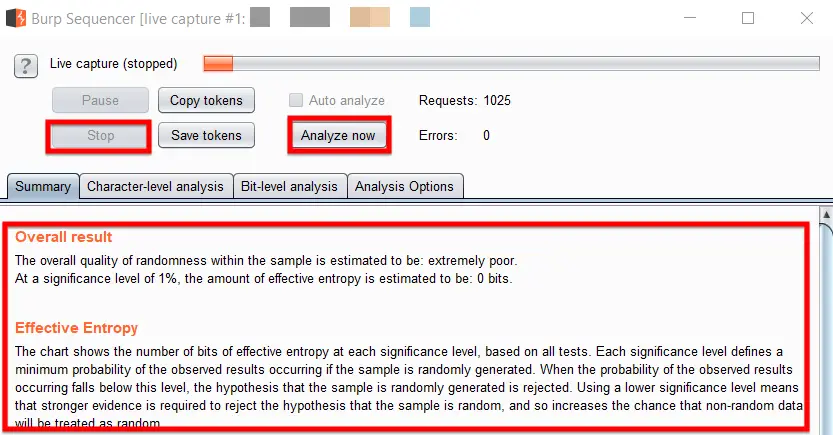
Now the Sequencer will repeatedly send the request, thus obtaining a high number of session IDs. The recommended amount to capture is a minimum of 1000 session IDs for an accurate analysis. Once it reaches 1000, click the Stop button and click “Analyze Now” button, it will provide the result through various statistical tests to determine the randomness.
Decoder
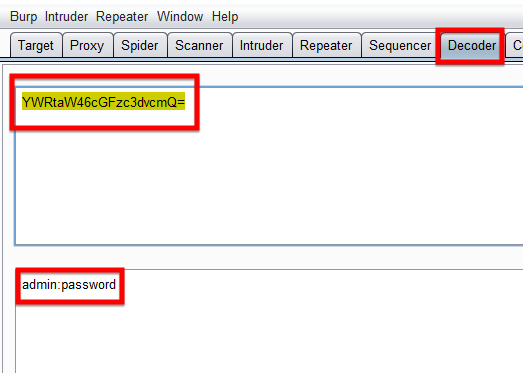
The Decoder feature is used to decode or encode the data between the different types of encoding schemes. You can enter the encoded data into the encoded field and decode it into plaintext or any other encoding you like. In this Burp Suite tutorial, I have decoded a Base64 encoded string and decoded it into plaintext. You can do the same vice versa.
Comparer
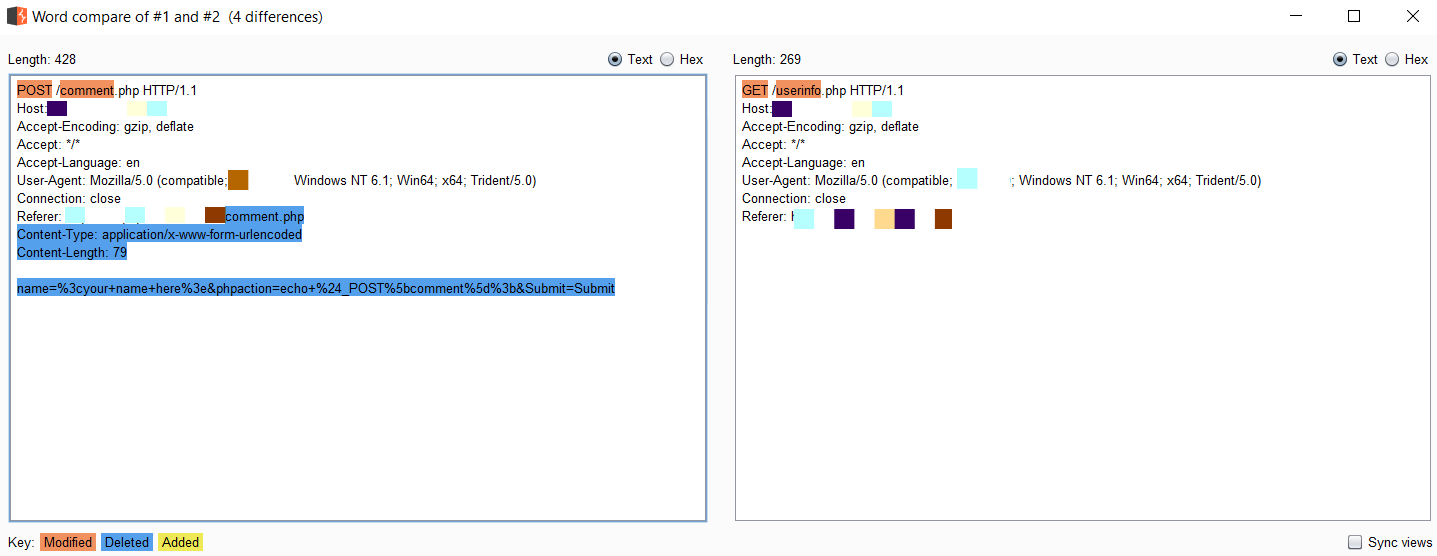
The Comparer is the feature of Burp Suite which is used to perform a comparison between any two requests, responses or any other form of data. It could be useful when comparing the responses with different inputs or results. It will show the comparison in the highlighted color.
Using the Third Party Extension
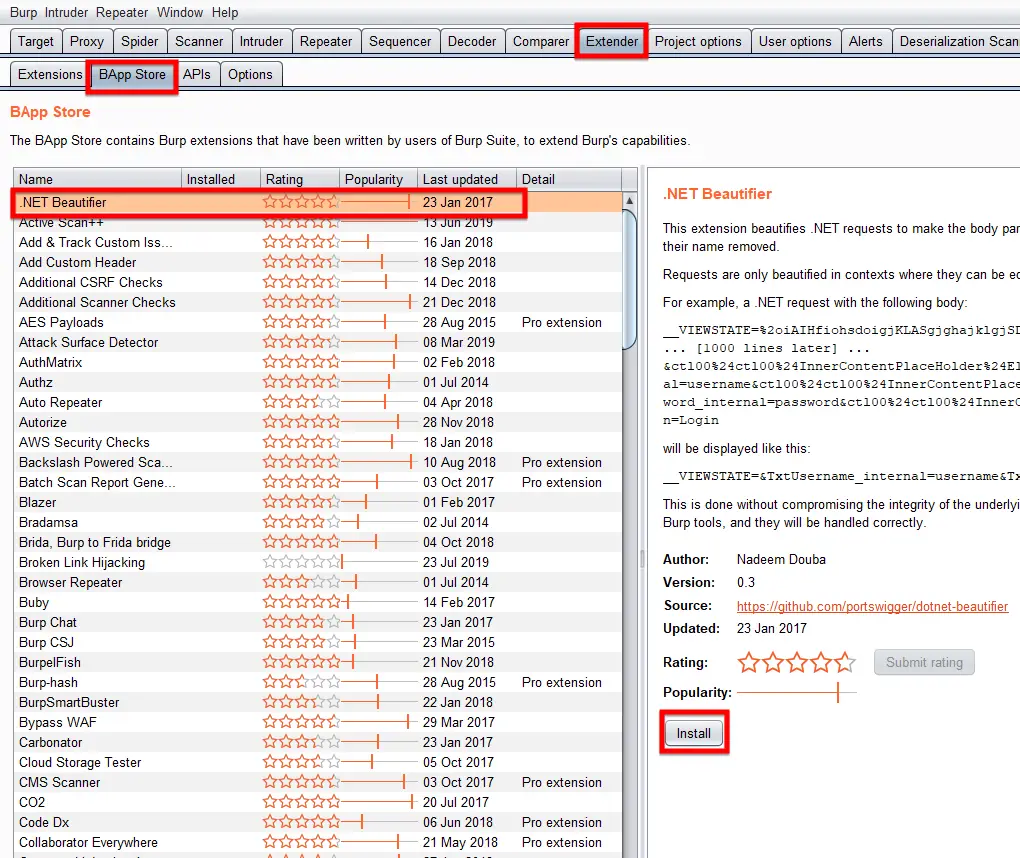
Burp extensions are made to enhance the capability of Burp Suite by including the extension in the Burp Suite framework that were developed by other Pentesters. Click on the Extender tab within Burp Suite and click the BApp Store sub-tab and select your desired extension which you like to add and click “Install” to add it to the Burp Suite.
Exporting the Results
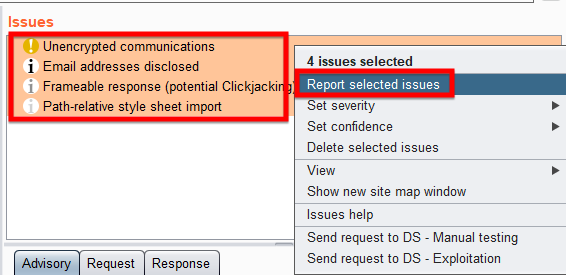
Once you have collected all the results, you might want to generate some reports. There are two reports available, HTML and XML. To create a report, select all the issues which you want to be included in the report, then press right click and choose “Report selected issues”.
Go through the Wizard and select which items you want in your report and which format. The HTML report can be open in the browser and while the PDF report will require a PDF file reader software.
Saving the Burp Session
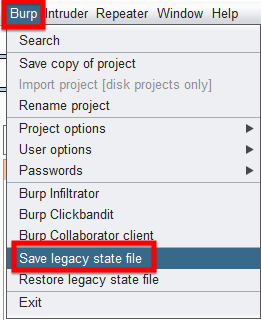
Many times during a penetration test, it is necessary to pause or hold the assessment and continue any time later, or you will be required to share your session with another security analyst. In these situations, the easiest thing is to save a local copy of your session. You can do this by selecting “Save legacy state file” from the Burp menu at the top.
It will create a flat file which you can restore at any point or share with anyone another consultant.
Conclusion
This Burp Suite tutorial has covered a lot of details, and hopefully, after reading this article, you would feel confident while performing a Web Application Penetration Test. We have even a tutorial on Burp Suite that is demonstrating how you can use it in different scenarios which you can find here. You should also experiment with all the features of Burp Suite and test them hands-on. And do comment below, tell us how was your experience going through this tutorial.