Welcome back, everyone. After learning how to scan for open ports with Netcat, we will now also learn how to check protocol versions with Netcat.
Netcat is a really useful and quick tool if you have no time to wait for an intense Nmap scan to finish. In this tutorial, we first will use the technique from yesterday to scan for open ports and then we will try to find out which Service Version, for example, SSH is using.
Let’s dive right in.
Table of Contents
Step 1 – Scan for Open Ports using Netcat
Open a terminal window on your favorite Security OS. I am using ParrotSec at the moment.
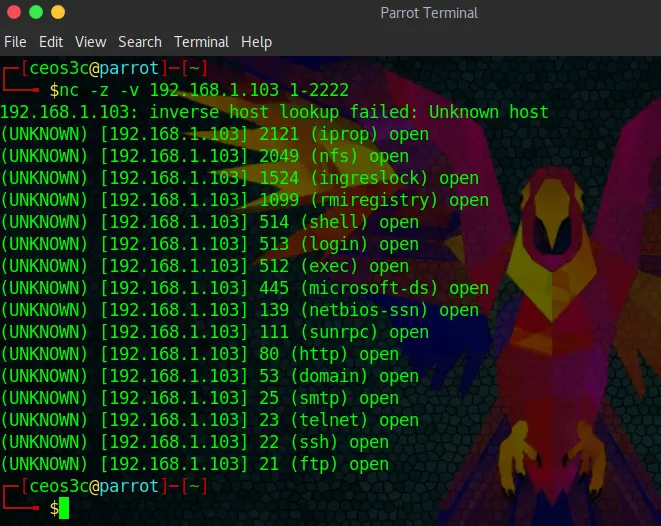
In this example, I scan an instance of Metasploitable 2 for open ports in the range between 1 and 2222.
nc -v -z 192.168.1.103 1-2222Code language: CSS (css)Now we can see that there are lots of open ports in that range. We are now going to verify the version of a few of them, also using Netcat.
Step 2 – Check Protocol Versions with Netcat
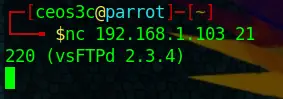
Let’s start at the bottom, with port 21 for FTP.
nc 192.168.1.103 21Code language: CSS (css)And we get returned the vsFTPd version 2.3.4
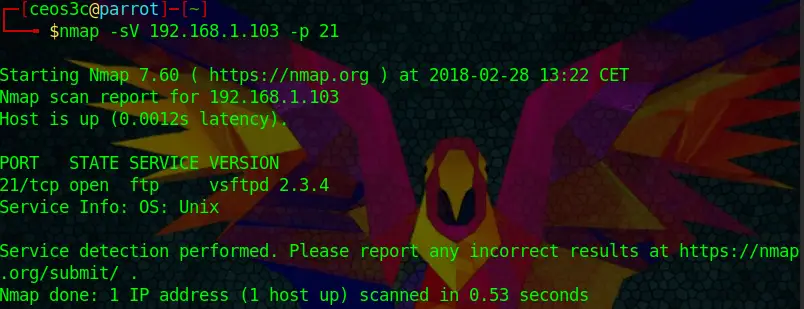
Let’s run the equivalent syntax in Nmap to verify our findings.
nmap -sV 192.168.1.103 -p 21Code language: CSS (css)And we got a positive. Nmap shows the same result.
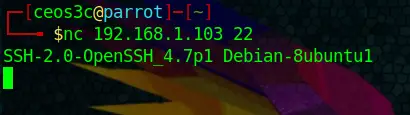
Let’s just run our Netcat command against the SSH port 22, just for the heck of it.
nc 192.168.1.103 22Code language: CSS (css)And sure enough, we got back the SSH version. We are not going to verify with Nmap again; I can confirm that the version is correct. Now be aware that this information is not always correct; depending on the system you are scanning, you can get false positive results. But it can give you a good idea of which kind of ports are probably open and what versions the services are running.
The takeaway from this is also to look at other tools; they might prove useful at some point. The bigger your portfolio is, the better.
Until next time.