Time to talk a little bit about the different Phases of a Penetration Test and shed some light on the typical penetration tester workflow.
A Penetration Test is usually split into different Phases.
Of course, you could just fire up Armitage and go haywire, but no professional Penetration Tester would ever do that.
It’s like an Elephant walking on Porcelain, whereas a professional would try to be as quiet as possible. There is a Gold Standard on how to approach a Penetration Test; it’s called PTES, or long: Penetration Testing Execution Standard. It consists of seven Phases. I encourage you to read through the PTES Technical Guidelines.
You can also have a more in-depth look at each individual step here.
Table of Contents
- Phase 1 – Pre-engagement Interactions
- Phase 2 – Intelligence Gathering
- Phase 3 – Threat Modeling
- Phase 4 – Vulnerability Analysis
- Phase 5 – Exploitation
- Phase 6 – Post Exploitation
- Phase 7 – Reporting
- Add your own Phases
- Different Standards
The 7 Phases of PTES
So, let’s have a look at the seven different Phases, and then we will talk about each step in particular.
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
I will try to give you a TL;DR of all of them.
Phase 1 – Pre-engagement Interactions
These are basically the Terms you settle on with your Client. It defines the Scope of the Penetration Test, the Hourly Rate of your Work, Time Estimation, and the General Rules of Engagement. This part is often overlooked, but it is one of the most important Phases.
It is really important to understand what a client expects from a Penetration Test and also to outline how the Penetration Tester should spend their costly time.
Phase 2 – Intelligence Gathering
This Phase of the Test is devoted to collecting as much information as possible on your Target. OSINT, or Open Source Intelligence, is a form of reconnaissance that involves finding, selecting, and acquiring information from publicly available resources such as Social Media Profiles, Websites, etc.
Intelligence Gathering is used to discover different entry points into an organization through either Physical, Electronic, or Social(Human) channels.
Phase 3 – Threat Modeling
The third Phase is dedicated to defining a threat modeling approach as required for the correct execution of a Penetration Test. Threat Modeling is a process by which potential threats, such as Structural Vulnerabilities, can be identified, enumerated, and prioritized.
Everything from a hypothetical attacker’s point of view. The whole point of this is to provide the defender with a systematic analysis of the probable attacker’s profile, the most likely areas of attack, and the assets that are most desired by an attacker.
Phase 4 – Vulnerability Analysis
Now we come to the more exciting part – Vulnerability Analysis. A Vulnerability Analysis is used to discover flaws in systems and applications which can be leveraged by an attacker.
These flaws can be anything from host and service misconfiguration, insecure application design, unpatched systems, and so forth.
There are two kinds of Vulnerability Analysis: Active and Passive.
Active would be a direct interaction with the tested device, and Passive would be, for example, Metadata Analysis or Traffic Monitoring.
The active analysis is naturally more likely to be discovered than the Passive.
Phase 5 – Exploitation
Let the games begin! The part we all enjoy the most – Exploitation.
This is where we actively try to penetrate a system. If you performed the prior Phase properly, you should know exactly where to attack first.
The main point is to identify the main entry point into an organization and to identify high-value target assets.
Phase 6 – Post Exploitation
The purpose of this Phase is to determine the value of the compromised machine and also to maintain control of it for later use by placing a Backdoor, for example.
The value of the machine is measured by the sensitivity of the data and the value of the machine to gain further access to the network.
In this Phase, you will already start documenting those things. It is very important to write down your findings, always keeping the Rules of Engagement in mind.
Phase 7 – Reporting
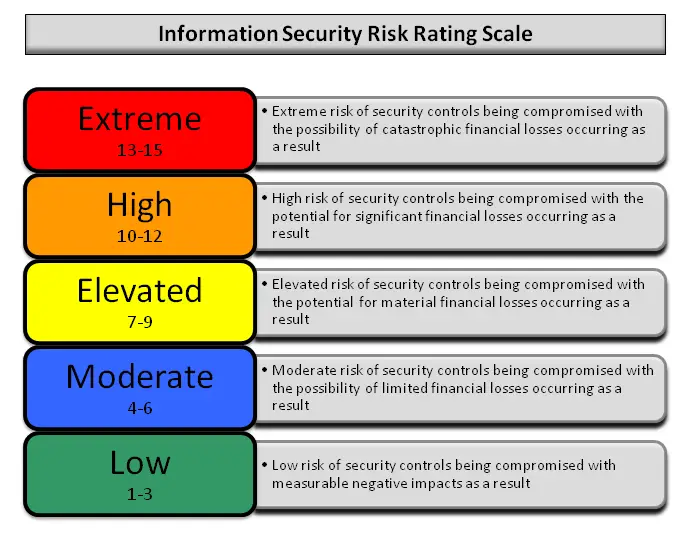
This Phase, as its name says, is the Reporting Phase and, at the same time the most valuable Phase for your client. This is where you document all your findings, ranked by Risk Level.
For this, the Information Security Risk Rating Scale can be used:
The Report is broken down into two major sections: The Executive Summary and the Technical Report.
The intended audience for the first would be those in charge of the oversight and strategic vision of the security program.
The intended audience of the latter would be those in charge of the actual network.
Add your own Phases
This is in no way set in stone. It’s a great starting guideline, but you can add Phases as you see fit.
For example, you could add things like Local/Network Enumeration, Local Privilege Escalation, Domain Privilege Escalation, and so on as separate Phases.
Different Standards
Also, this is not the only Standard there is. Here in Germany, for example, we have a 5 Phase Standard set by the BSI, the “Bundesamt für Sicherheit in der Informationstechnik”, which roughly translates to Government Institution for Security in Information Technology.
Their 5 Phase Model looks like this:
- Preparation
- Information Gathering and Analysis
- Evaluation and Risk Analysis
- Active Exploitation
- Final Analysis
So as you can see, there are a couple of ways how to approach things.
I hope this article sheds some light on how those things work and maybe also helps you to structure your workflow.
It is essential to document every detail so your client is able to fix holes in their security.