In this guide, I will show you how backup your pfSense Configuration and why it is important to do so.
Especially if you experiment around a lot, it’s an easy way to restore back to a working configuration. I had to use this feature many times and I usually keep my backups of a few different states.
This is extremely important. I already put lots and lots of hours into configuring pfSense to have it where I want it to be. This is not only hours of configuration, but hours and hours of research.
Also, do a backup each and every time before upgrading to a newer version of your firewall. I learned this the hard way with my NAS just a few weeks ago. I will never run an upgrade without pulling a backup right before I run the upgrade.
Let me walk you through the process real quick.
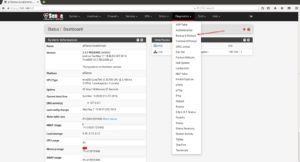
On your pfSense firewall navigate to Diagnostics -> Backup & Restore
You see, there aren’t too many options so you don’t need to be scared of this backup process 🙂
Let’s go through the options real quick starting on the top:
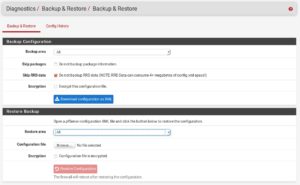
- Backup Area
Here you can choose to backup just certain settings isolated, you can backup:
- All (the obvious choice for us)
- DNS Resolver
- DHCP Server
- DHCPv6 Server
- Interfaces
- NAT
- RRD Data
- Scheduled Tasks
- System
- SNMP Server
I always simply do a Backup All, because I have no reason to specifically backup only single areas.
- Skip packages
This allows you to Skip installed packages in your backup. If you have Squid Proxy installed, for example, it wouldn’t back that up. We do not want this, so we keep this box unticked.
- Skip RRD data
RRD Data are your Graphs. Like the traffic Graph for example. I do not back them up in my home, I do not need them. In a corporate environment, you might want to back them up.
- Encryption
This goes without thinking. Always encrypt your backups with a password.
You see? No magic here. Now, after we set everything up correctly, click on Download configuration as XML. That´s really it. Store the backup file on a storage of trust, you can use Dropbox or Google Drive for it, although you should use a very strong password for those services.
Now let us get into Restore Backup.
As you can see below, there is an option to restore your backup. This is really easy. You just choose the configuration file, tick the encryption box, enter your password and hit restore.
After a reboot, you are back to your old config.
You can even choose a Restore area to specifically just restore your DHCP server. You do not even have to run a full restore, isn’t this awesome?
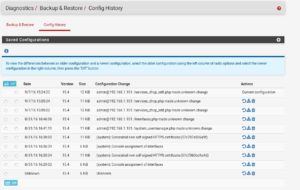
Let´s switch over to the Config History tab.
Now, this is a really convenient feature of pfSense. Every time you make a change in your configuration, pfSense automatically makes a backup. With this, even if shit hits the fan and you just did something very bad without pulling a backup before, you can still revert back to a still working state. The amount of configs saved here is limited, so don´t rely on it! It´s simply an emergency tool.
You can even see what changes were made between 2 different configuration states, to do so, just select two different configs on the buttons on the left and hit Diff.
You get a more complicated looking output then, but you can actually see what was changed. I will not go deeper into this, maybe I cover it in a separate article.
This much for backing up guys, always do your backups religiously. Especially before updating to a newer version of your firewall. It’s a lifesaver!
Video:
https://www.youtube.com/watch?v=tJYHREVdHB0
- Firewall Micro Appliance With 4x Gbe Intel Lan Ports for PFSense
- Firewall Micro Appliance with 2x Gbe Intel LAN Ports for PFSense Barebone
- Firewall micro appliance with 4x Gigabit Intel LAN Ports for pfSense with 4GB RAM / 16GB mSATA
- Firewall micro appliance with 2x Gigabit Intel LAN Ports for pfSense with 2GB RAM / 16GB mSATA