In this tutorial, you will learn what Domain Overrides are and how they work. You will also learn about Host Overrides and how to set these up using the pfSense firewall. Domain overrides are an important feature when configuring DNS servers.
Table of Contents
👀 This Tutorial has some related Articles!
👉 The Complete pfSense Fundamentals Bootcamp
👉 Install pfSense from USB – The Complete Guide
👉 Install pfSense on VirtualBox
👉 The Complete pfSense OpenVPN Guide
👉 The Complete pfSense DMZ Guide
👉 Generate SSL Certificates for HTTPS with pfSense
👉 The Complete pfSense Squid Proxy Guide (with ClamAV!)
👉 pfSense Site-to-Site VPN Guide
👉 pfSense Domain Overrides Made Easy
👉 pfSense Strict NAT (PS4,PS5,Xbox,PC) Solution
👉 The Best pfSense Hardware
👉 Traffic Shaping VOIP with pfSense
👉 pfSense OpenVPN on Linux – Setup Guide
👉 pfSense Firewall Rule Aliases Explained
👉 Email Notifications with pfSense
👉 pfSense DNS Server Guide
What are Domain Overrides
To put it in one sentence, Domain Overrides are used to configure specific DNS Servers for particular domains. For example, let’s assume the following setup:
- pfSense: 192.168.1.1 – DNS Server for your local network
- Windows Server: 172.16.0.10 // AD Domain: mycompany.com
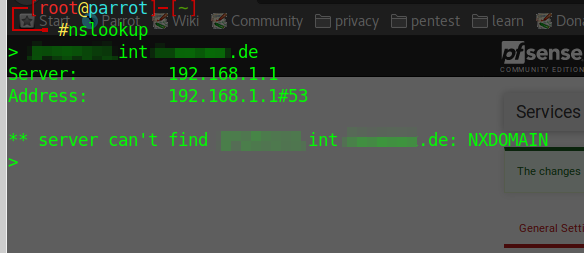
Now you want to forward every request that goes to mycompany.com to the IP of your Windows AD Server with the IP of 172.16.0.10. If you would run this setup without a Domain Override and you want to look up a hostname residing in the domain like server.mycompany.com, you would get a Host server.mycompany.com not found: 3 (NXDOMAIN) error.
I’ll demonstrate it with an example of one of my own servers:
nslookup without Domain Override
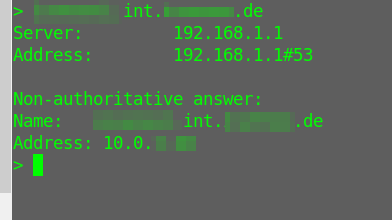
nslookup with Domain Override
As you can see, after setting the Domain Override pfSense forwards the request to the Domain Name Server. So how to set up a Domain Override?
⚠️ If you would like to learn more about pfSense, I highly recommend you check out my pfSense Fundamentals Bootcamp over at Udemy. This is the most up-to-date as well as the highest-rated pfSense course on Udemy.
Setting up Domain Overrides
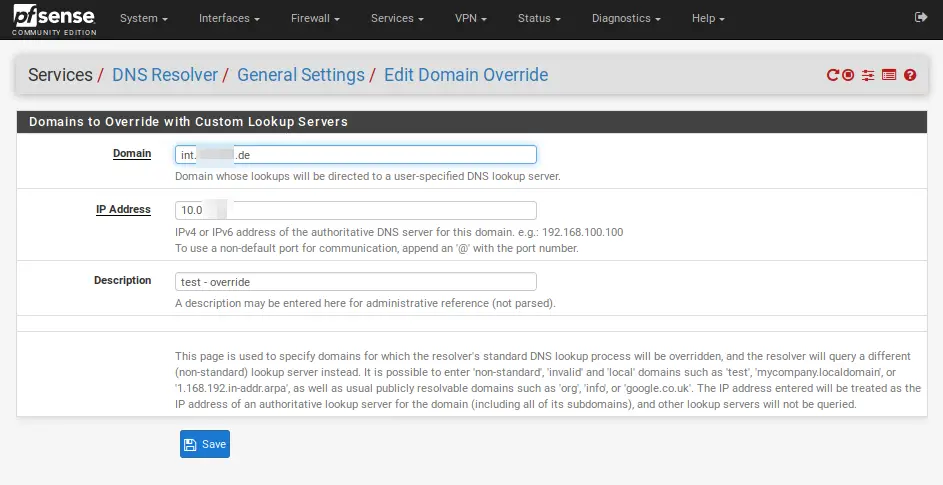
It’s child’s play. Simply navigate to Services / DNS Resolver, scroll all the way to the bottom and click on +Add underneath Domain Overrides. Now you got to enter your Domain Name and the IP Address of your Domain Controller or DNS Server you want to forward your queries to. Click on Save and Apply Changes.
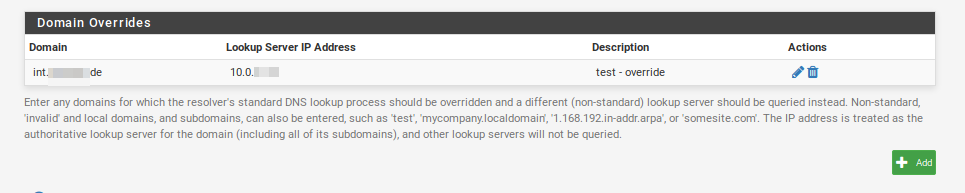
If you did everything correctly, you can verify your settings:
And that’s all there is to it, easy, right?
Now, while we are at it, let’s also cover Host Overrides, you have probably seen the option right above Domain Overrides already.
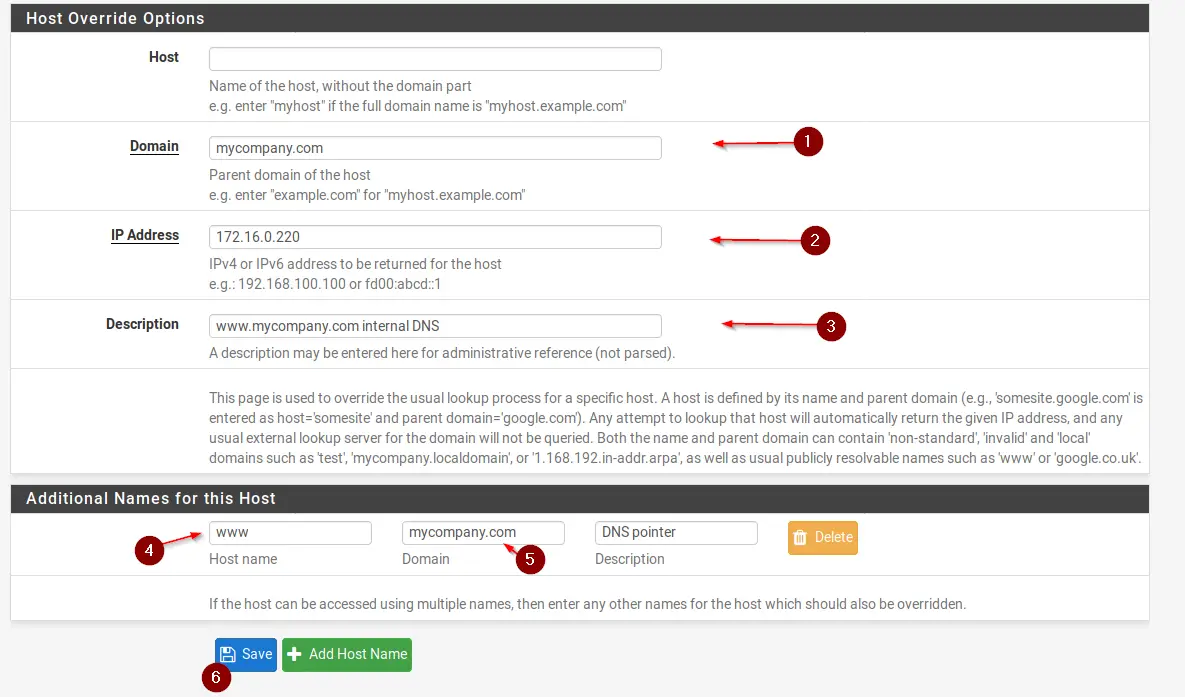
Host Overrides
Host Overrides are used to configure how a specific hostname is resolved by pfSense’s DNS Resolver. One use-case would be split DNS, so you can resolve your Public DNS hostnames to private IP Addresses, so you can eliminate the need for NAT reflection.
Let’s assume we have a website hosted on another local network with the Subnet of 172.16.0.0/24. The website address is www.ourcompany.com and resolves to 172.16.0.200. Without NAT reflection, clients in our local 192.168.1.0/24 Subnet will not be able to reach the website. So what we need to do is, we need to create a host override on our local 192.168.1.0/24 Subnet for www.ourcompany.com pointing to its IP Address of 172.16.0.200.
Let’s visualize it to understand it better.
Navigate to Services / DNS Resolver and scroll down to the bottom. Underneath Host Overrides, click on +Add.
Wrapping up
Once you wrapped your head around it, it’s pretty straightforward and easy to understand. Domain and Host Overrides are useful tools within pfSense, especially if you run your firewall in a corporate environment. Are you using Domain and Host Overrides? Let me know in the comment section below.


Pro Tip: if you use Domain Over-Rides for a Windows Domain Controller, remember to add a Reverse Lookup Domain Over-Ride also, ie. like 1.168.192-in-addr.arpa and your Domain Controller IP addr.
I beat my head against the wall on this issue, ie, using pfSense with a Windows Domain control, until the light went on.
My setup is probably typical for a small Windows Domain Controller with a pfSense firewall. To get workstation to work with the Domain Controller(Active Directory and Group Policies) you must point your workstations to the Domain Controller as their Primary DNS server. But what if you want pfSense’s pfBlockerNG to work, it needs the pfSense DNS to work, or what if you need pfSense to preform DNS over TLS, so what do you do, you add a DNS forwarder to the Windows Domain Controller, pointing to pfSense. This works great as expected, pfBlockerNG works, DNS over TLS works, workstatation work and can resolve the Windows Domain resources(remember the workstation point their DNS to the Domain Controller). All is well until you add a pfSense program like NTopNG that runs on pfSense. Well I should backup a little, my pfSense install doesn’t have the same domain as Windows Domain, this is by design so that it is stand alone(might be other reasons but this is my setup), so I have a windows domain like mydomain.local, and pfSense has mypfsense.mylocal. The question that arises is from pfSense how do I resolve Domain IP’s in NTopNG that resides on the Domain Controller. The obvious answer is add a DNS Domain Override to the DNS Resolver(unbound), like if you want to resolve workstations on the Windows Domain Controller, mydomain,local then go to the Domain Controller. So if host.mydomain.local go to 192.168.1.1(my domain for example only). This works as expected when using pfSense’s DNS lookup, NSLookup or Dig from a workstations, things are great, right?? Except NTopNG wants to do Reverse Lookup, opps, how doesn’t resolve, even using NSlookup or Dig to the pfSense DNS doesn’t work with Reverse Lookups.
This is what set me on a research path to this posting. To make the answer short, to do reverse lookups using pfSense DNS(unbound), you also need to add an Domain Over-ride for the PTR records, so you enter the Over-ride as:
Windows Domain PTR – 1.168.192-in-addr.arpa, and DC DNS – 192.168.1.1, now everything will resolve as it should.
Note: you might also need to fiddle with the Resolver(unbound) network setting a little to resolve also, but usually ALL/ALL works, just check for WAN DNS request leakage inbound.
Hope this helps someone,
Wayne
When I use Host Override, it blocks facebook and youtube forever?
How can I undo a Host Override? I deleted rules and overrides already but the sites are still blocked.
Hello so if I’m using my own internal active directory DNS I have to use the Domain Override?