Many of you asked me to create an easy-to-understand step-by-step tutorial on how to create a pfSense site-to-site VPN tunnel between two pfSense firewalls. I try to make it as simple as possible.
Table of Contents
- The Scenario: pfSense Site to Site VPN
- Step 1 – Creating IPSec Phase 1 on pfSense #1 HQ
- Step 2 – Creating IPSec Phase 2 on pfSense #1 HQ
- Step 3 – Creating a Firewall Rule on pfSense #1 HQ
- Step 4 – Creating IPSec Phase 1 on pfSense #2 Remote Location
- Step 5 – Creating IPSec Phase 2 on pfSense #2 Remote Location
- Step 6 – Creating a Firewall Rule on pfSense #2 Remote Location
- Step 7 – Testing the Tunnel
- Conclusion
👀 This Tutorial has some related Articles!
👉 The Complete pfSense Fundamentals Bootcamp
👉 Install pfSense from USB – The Complete Guide
👉 Install pfSense on VirtualBox
👉 The Complete pfSense OpenVPN Guide
👉 The Complete pfSense DMZ Guide
👉 Generate SSL Certificates for HTTPS with pfSense
👉 The Complete pfSense Squid Proxy Guide (with ClamAV!)
👉 pfSense Site-to-Site VPN Guide
👉 pfSense Domain Overrides Made Easy
👉 pfSense Strict NAT (PS4,PS5,Xbox,PC) Solution
👉 The Best pfSense Hardware
👉 Traffic Shaping VOIP with pfSense
👉 pfSense OpenVPN on Linux – Setup Guide
👉 pfSense Firewall Rule Aliases Explained
👉 Email Notifications with pfSense
👉 pfSense DNS Server Guide
The Scenario: pfSense Site to Site VPN
I try to keep this example scenario as simple as possible, therefore I created an easy-to-understand, self-explaining diagram.
This should give you a pretty good understanding of what we want to achieve. We simply want to establish a pfSense site-to-site VPN connection between pfSense #1 HQ and pfSense #2 Remote Location. To do this, we need to create IPSec tunnels and firewall rules on both sides. I kept the subnets simple so you don’t get confused by too many different IPs. The Gateway in your case would be your WAN IP Address.
Without further ado, let’s get right started.
Step 1 – Creating IPSec Phase 1 on pfSense #1 HQ
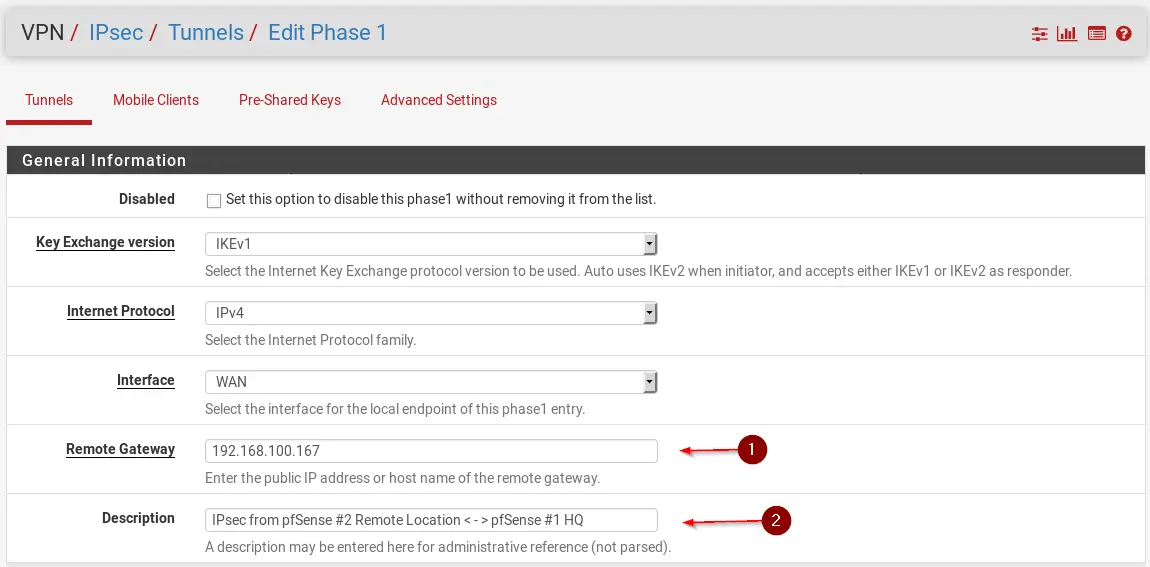
To create a pfSense site-to-site VPN, you need to log in to your pfSense #1 HQ and navigate to VPN / IPsec and click on + Add P1. Set the address of the Remote Gateway and a Description.
- IP of your WAN Interface on your pfSense #2 Remote Location
- Enter a Description
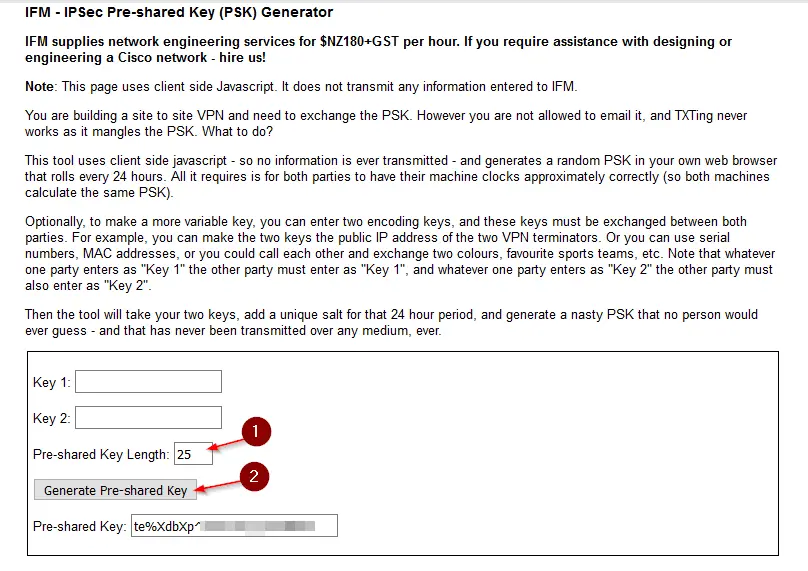
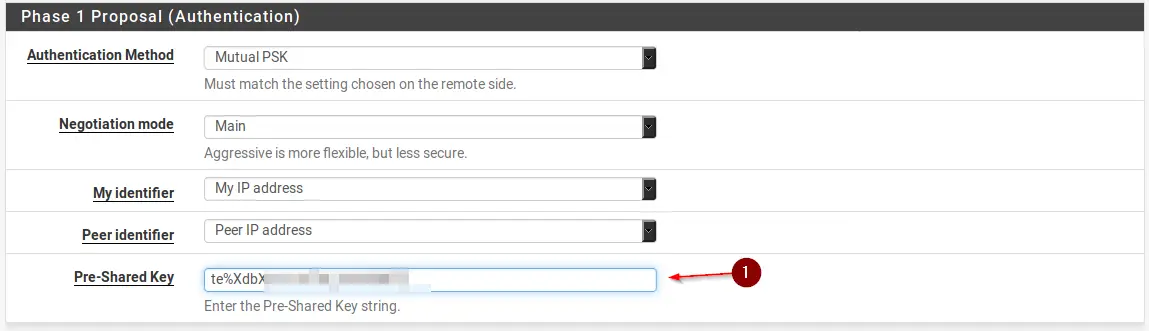
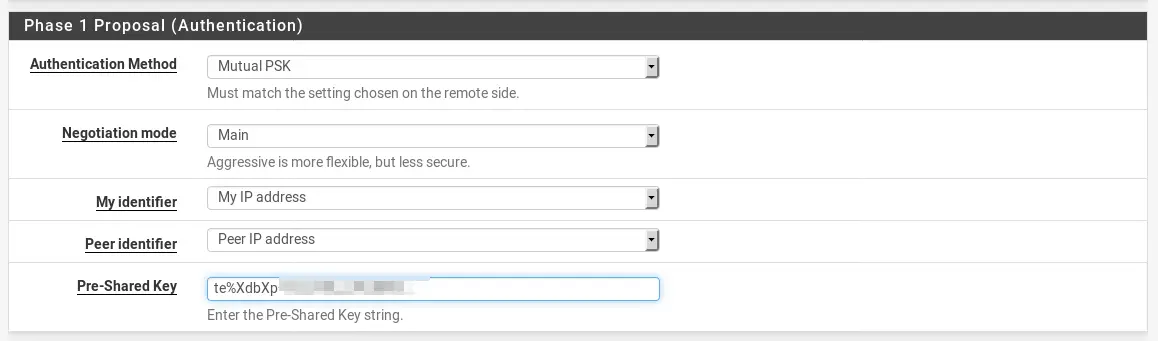
Scroll down to Phase 1 Proposal (Authentication). Now head to any page you like, or this one, to create a Pre-Shared Key.
You can also use the tool pwgen on Linux with the following command to create a key:
pwgen -sy 25Copy this key and paste it into the Pre-Shared Key field.
Scroll down to the bottom leaving everything else on Default and click Save. Click Apply Changes after.
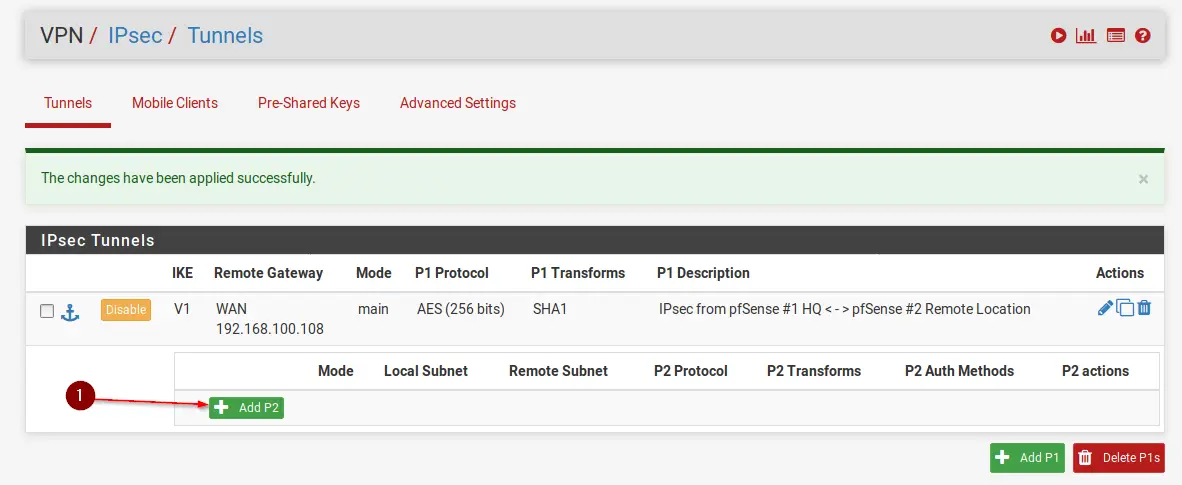
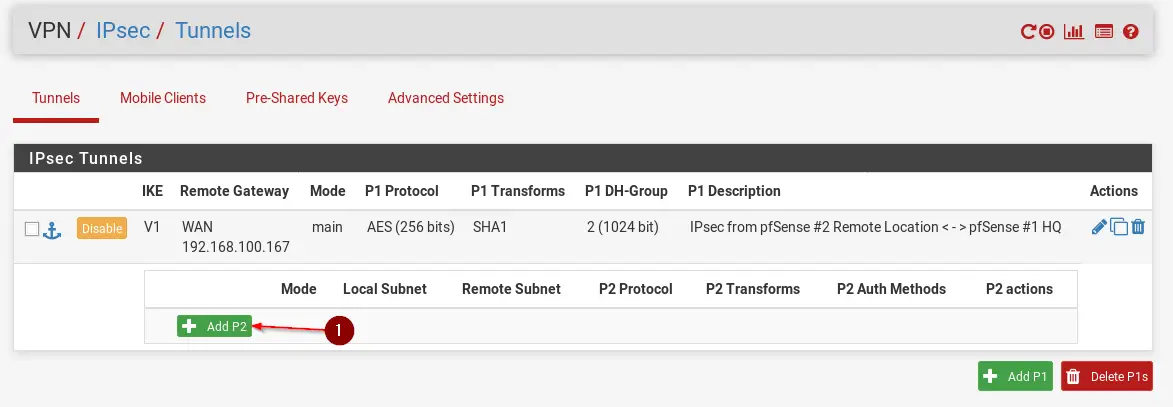
Step 2 – Creating IPSec Phase 2 on pfSense #1 HQ
Time to create the second Phase. Click on + Show Phase 2 Entries and click on + Add P2.
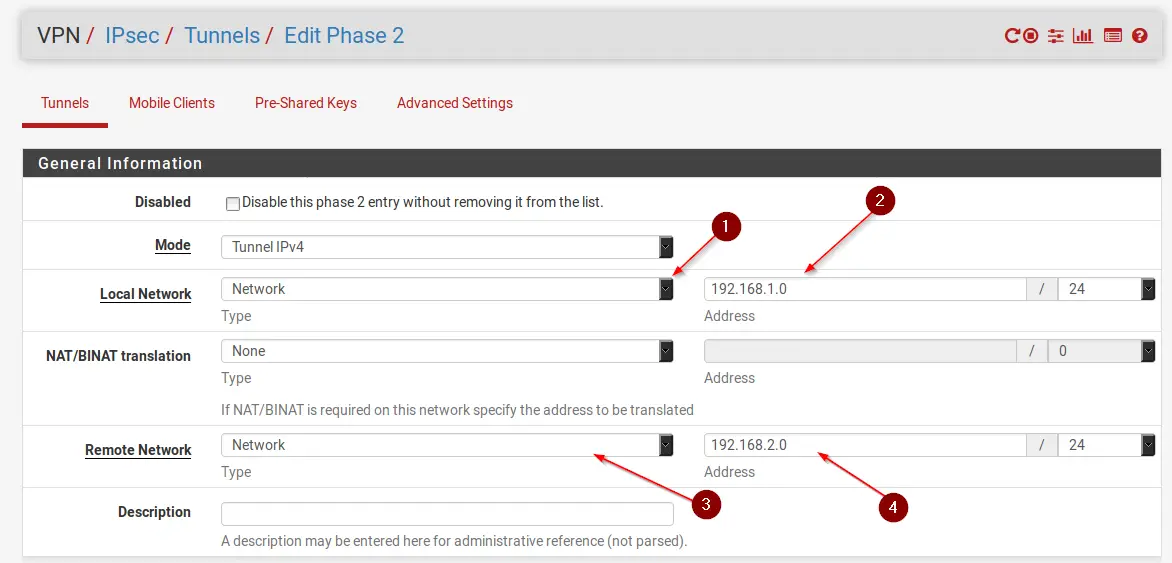
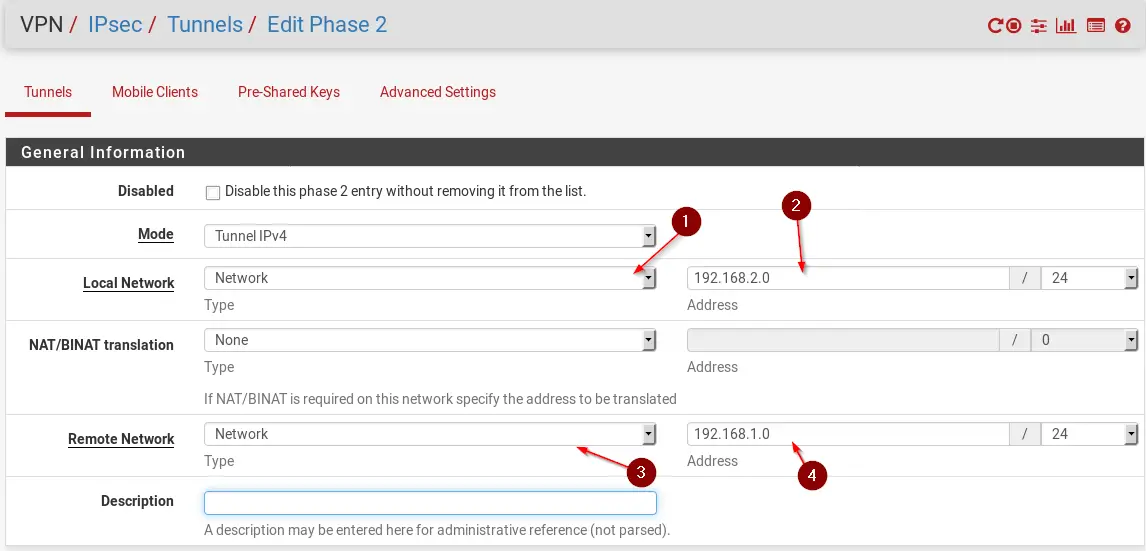
Now enter values like in the following example:
- On Local network choose Network
- Enter the Subnet of your Local Network (192.168.1.0/24 for pfSense #1 HQ)
- On Remote Network choose Network
- Enter the Subnet of your Remote Network (192.168.2.0/24 for pfSense #2 Remote Location)
Enter a description if you want.
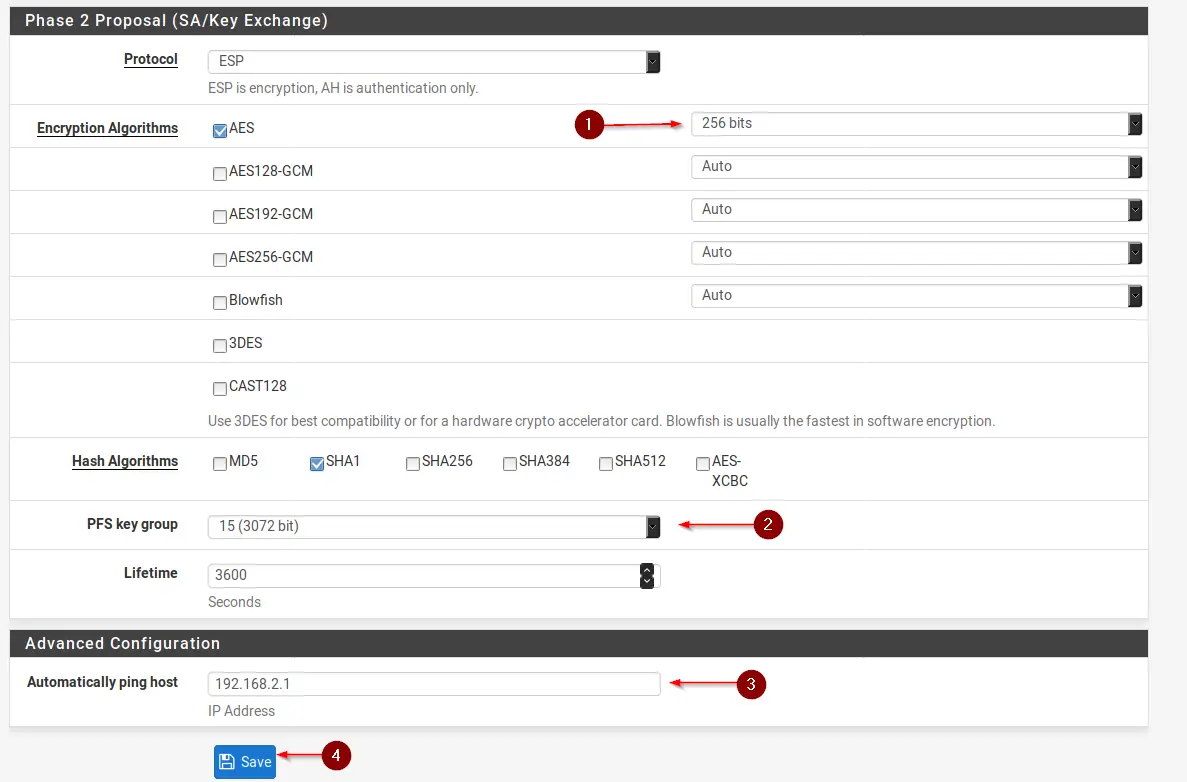
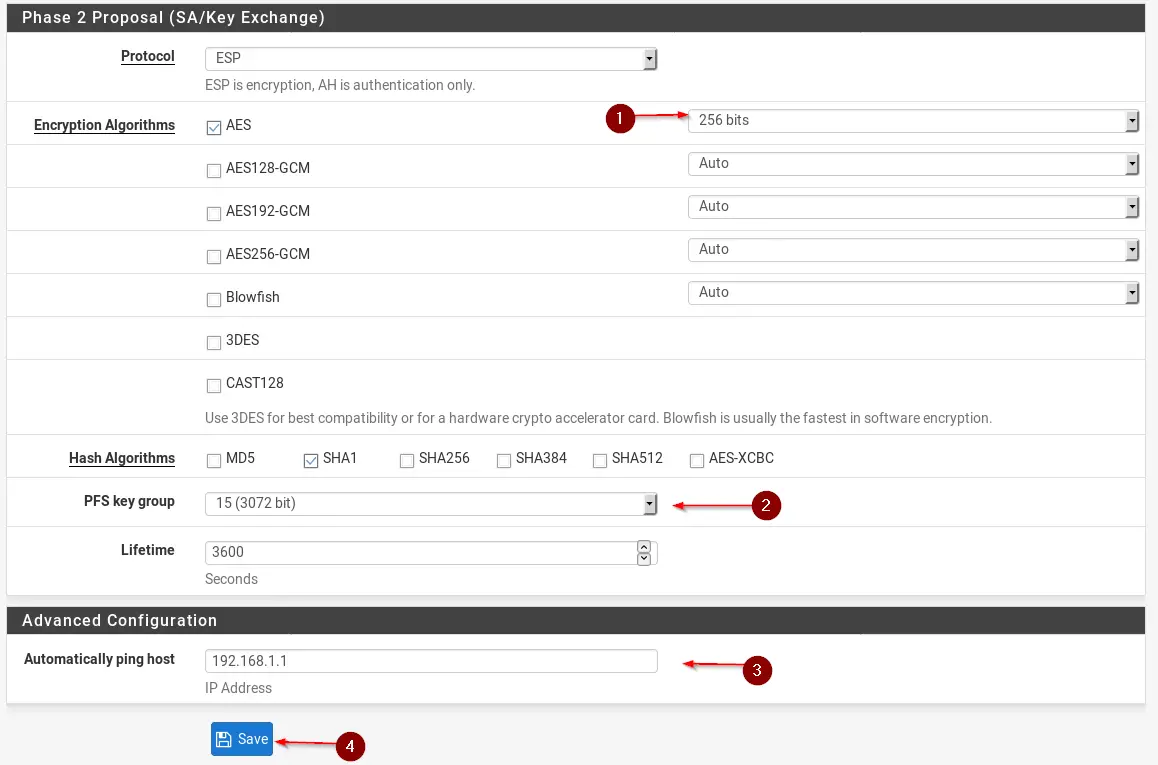
Scroll down to Phase 2 Proposal (SA/Key Exchange). Enter values like in the following example:
- Change AES Encryption to 256 bits
- Change PFS key group to 15 (3072 bit)
- Enter the pfSense #2 Remote Location’s IP Address to be pinged automatically (this ensures that the tunnel stays active at all times)
- Smash that Save button (Sorry, watched too many YouTube videos)
- Hit Apply Changes
Almost done with pfSense #1, now we just need to create a Firewall Rule for the IPsec interface.
Step 3 – Creating a Firewall Rule on pfSense #1 HQ
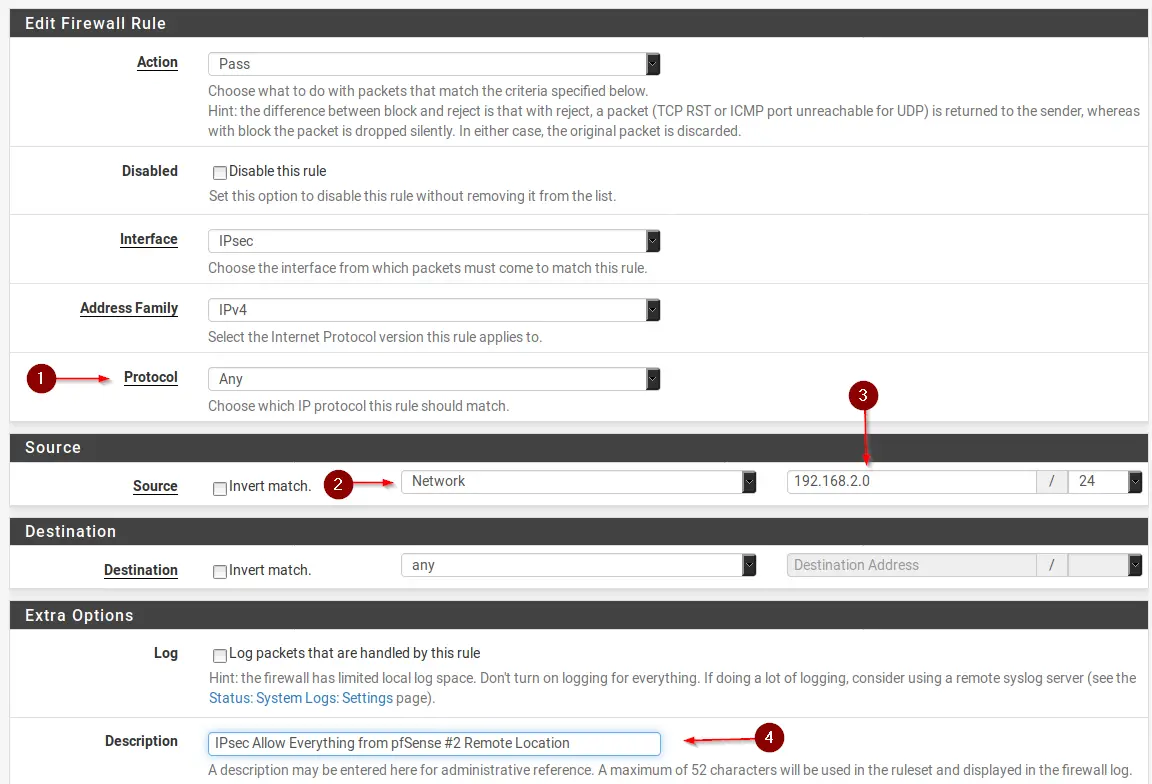
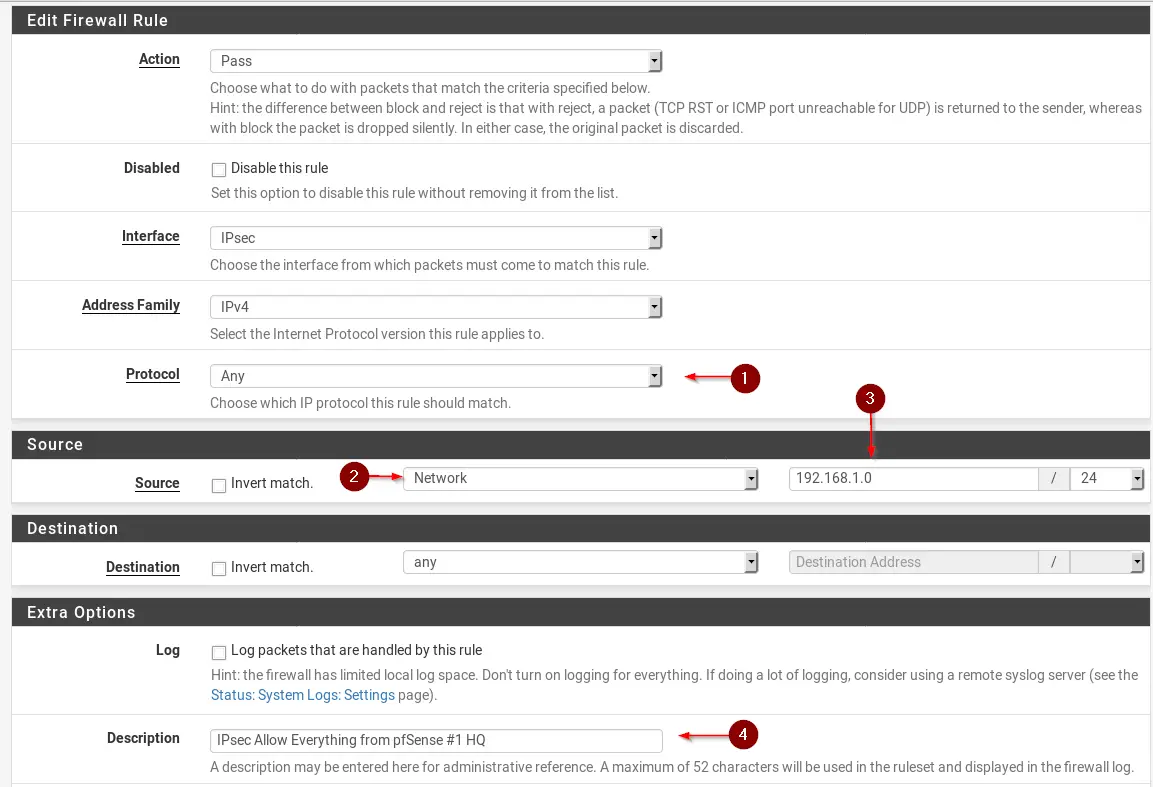
Navigate to Firewall / Rules / IPsec. Click on Add. Enter values as the following:
- Change Protocol to Any
- For Source select Network
- Enter the Subnet of pfSense #2 Remote Location (192.168.2.0/24)
- Enter a Description
- Hit Save & Apply Changes
That’s it. We are done with pfSense #1 HQ, let’s head over to pfSense #2 Remote Location to create our pfSense site-to-site VPN.
Step 4 – Creating IPSec Phase 1 on pfSense #2 Remote Location
Now we basically need to repeat those exact steps again just with slightly changed values. I will guide you through every step anyway. Navigate to VPN / IPsec and click on + Add P1. Enter values as in the following:
- IP of your WAN Interface on your pfSense #1 HQ
- Enter a Description
Scroll down to Phase 1 Proposal (Authentication). Enter the same Pre-Shared Key like in pfSense #1 HQ that we created in Step 1.
Scroll to the bottom and hit Save & Apply Changes.
⚠️ If you would like to learn more about pfSense, I highly recommend you check out my pfSense Fundamentals Bootcamp over at Udemy. This is the most up-to-date as well as the highest-rated pfSense course on Udemy.
Step 5 – Creating IPSec Phase 2 on pfSense #2 Remote Location
Once again, click on +Show Phase 2 Entries and click on + Add P2.
Now enter values like in the following example:
- On Local network choose Network
- Enter the Subnet of your Local Network (192.168.2.0/24 for pfSense #2 Remote Location)
- On Remote Network choose Network
- Enter the Subnet of your Remote Network (192.168.1.0/24 for pfSense #1 HQ)
Enter a description if you want.
Scroll down to Phase 2 Proposal (SA/Key Exchange) and enter the values like below.
- Change AES Encryption to 256 bits
- Change PFS key group to 15 (3072 bit)
- Enter the pfSense #1 HQ’s IP Address to be pinged automatically (this ensures that the tunnel stays active at all times)
- Hit Save & Apply Changes.
Step 6 – Creating a Firewall Rule on pfSense #2 Remote Location
Navigate to Firewall / Rules / IPsec. Click on Add. Enter values as the following:
- Change Protocol to Any
- For Source select Network
- Enter the Subnet of pfSense #1 HQ (192.168.1.0/24)
- Enter a Description
- Hit Save & Apply Changes
Now, in theory, a tunnel should be established between the two.
Step 7 – Testing the Tunnel
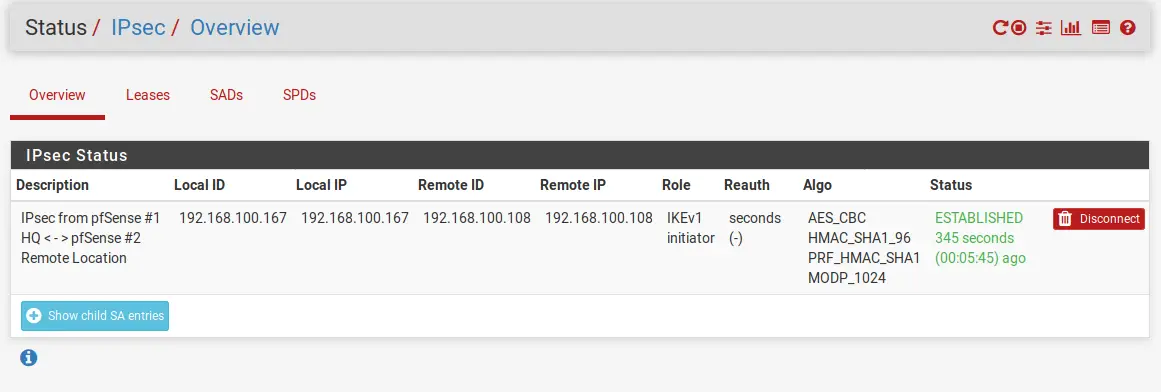
Back on pfSense #1 HQ head to Status / IPsec. You should see, if everything went well, that a connection is established.
You will see a similar picture on pfSense #2 Remote Location. We can do two more things to also validate if the firewall rules are correct: Running a Ping from a Client on each Firewall’s Subnet.
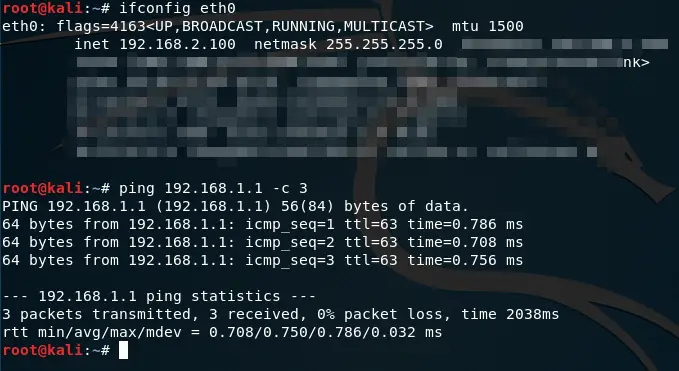
First I will try to Ping pfSense #1 HQ from a Client connected to pfSense #2 Remote Location.
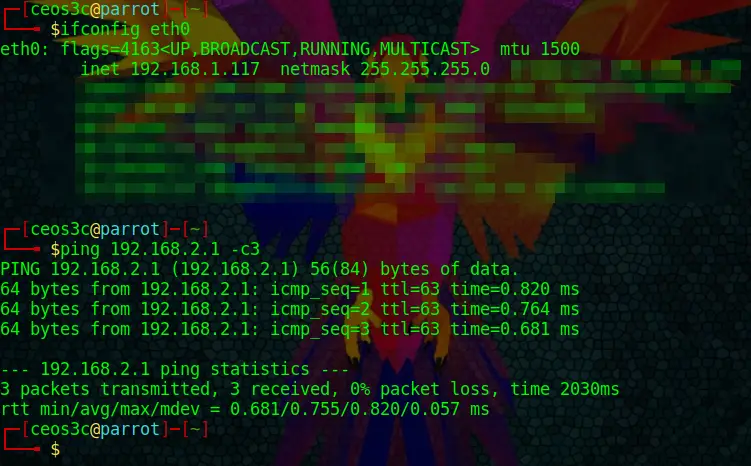
And now I run a Ping from a client connected to pfSense #1 HQ to pfSense #2 Remote Location.
Conclusion
And sure enough, you can see that a connection is established. And that’s it. That should give a good idea of how to create a pfSense Site to Site Tunnel with pfSense!
👀 This Tutorial has some related Articles!
👉 The Complete pfSense Fundamentals Bootcamp
👉 Install pfSense from USB – The Complete Guide
👉 Install pfSense on VirtualBox
👉 The Complete pfSense OpenVPN Guide
👉 The Complete pfSense DMZ Guide
👉 Generate SSL Certificates for HTTPS with pfSense
👉 The Complete pfSense Squid Proxy Guide (with ClamAV!)
👉 pfSense Site-to-Site VPN Guide
👉 pfSense Domain Overrides Made Easy
👉 pfSense Strict NAT (PS4,PS5,Xbox,PC) Solution
👉 The Best pfSense Hardware
👉 Traffic Shaping VOIP with pfSense
👉 pfSense OpenVPN on Linux – Setup Guide
👉 pfSense Firewall Rule Aliases Explained
👉 Email Notifications with pfSense
👉 pfSense DNS Server Guide




hey man, need your help
i have configured pfsense vpn/ipsec tunnel. ill explain my topology below and then tell you what i have done with pfsenses.
i have two networks
nat1->pfsense1->router1->mls1->pc1
nat2->pfsense2->router2->mls2->pc2
pfsense1-> wan=192.168.122.70 lan 192.1682.2
router e0/0 connected to pfsense1= 192.168.2.1 e0/1 connected to mls1 =192.168.10.1
mls1 e0/0 connected to router1 192.168.10.2 mls vlan 30 192.168.30.1
pc1 192.168.30.30 all /24
pfsense2 wan= 192.168.122.25 lan 192.168.3.3
router2 e0/0 connected to pfsense2 192.168.3.1 e0/1 connected to mls 2 192.168.20.1
mls2 e0/0 connected to router2 192.168.20.2 mls2 vlan 40 192.168.40.1
pc2 192.168.40.40 all /24
in my pfsense1-> vpn->ipsec->tunnel i have
remote gateway 192.168.122.25 and AES 256bits SHA256 DH Group 14 (2048) and lifetime 3600
and phase2
local network 192.168.30.0 /24, remote network 192.168.40.0 /24
firewall->rules->wan i have protocol any, source any, destination any
another protocol tcp, source any, destination any and destination port IPsec NAT-T (4500)
another protocol ESP, source any and destination any
and another protocol UDP, source any, destination this firewall (self) and the destination port ISAKMP(500)
firewall->rules->lan
protocol any, source network 192.168.2.0 /24, destination any
another protocol any, source network 192.168.30.0 /24 and destination any
another protocol any, source 192.168.10.0 /24 and destination any
firewall->rules->IPsec
protocol any, source network 192.168.30.0 /24 and source network 192.168.40.0 /24
another protocol any, source any, destination any
Pfsense2
in my pfsense2-> vpn->ipsec->tunnel i have
remote gateway 192.168.122.70 and AES 256bits SHA256 DH Group 14 (2048) and lifetime 3600
in phase2
local network 192.168.40.0 /24, remote network 192.168.30.0 /24
firewall->rules->wan i have protocol any, source any, destination any
another protocol tcp, source any, destination any and destination port IPsec NAT-T (4500)
another protocol ESP, source any and destination any
and another protocol UDP, source any, destination this firewall (self) and the destination port ISAKMP(500)
firewall->rules->lan
protocol any, source network 192.168.3.0 /24, destination any
another protocol any, source network 192.168.40.0 /24 and destination any
another protocol any, source network 192.168.20.0 /24 and destination any
firewall->rules->IPsec
protocol any, source network 192.168.40.0 /24 and source network 192.168.30.0 /24
another protocol any, source any, destination any
I want to know how to JOIN an IPsec Site to Site VPN with my PFsense, not create one. Where do I go to read about that?
I tried as you mention above but i am not able to connect with this method.
Same situation too :c I only see the gateway but i cant see my PC on the other site, can you resolve this?
Hi, greate guide. works nice but i got problem with routing, i can reach the gateway on both sites but nothing els behind.
Hi! I used to do this with “tunnel gre” protocol, and work so fine… I have 2 clients, with office (Miami-Caracas), but actually I dont know how tu applie QoS over tunnel gre…
You are awesome thank you for this guide ❤