I know, I know. The titles of my posts get out of hand, but it just so happens that I have started watching Ancient Aliens on Netflix in the past week. I think it’s a great fit! Anyway, back to the topic, the Ethical Hacking Diaries #4 and what I have learned in Week #13 of 2020 in my journey of becoming a Bug Bounty Hunter.
I got feedback on the blog through various social channels, some of them pointing out that the blog posts don’t need to be that long. Well, it so happens that I haven’t learned all that much last week due to a lot of workload in my day job, so this will be a shorter episode. I also planning (still) on doing accompanying videos on the YouTube channel. That might make things a bit less time consuming for me.
Burp Community Sucks
That’s kind of a stupid title because Burp Community is still great if you haven’t tried Burp Pro yet. Although last week my 30-day Burp Pro trial ran out and I had to go back to Burp Community. Running intruder was quite… infuriating. But more on that next week (I just pulled the trigger on a Burp Pro License as I’m writing this).
With that being out of the way, let’s have a quick digest of what I have learned in the past week.
Checking Commands that can be run as Sudo
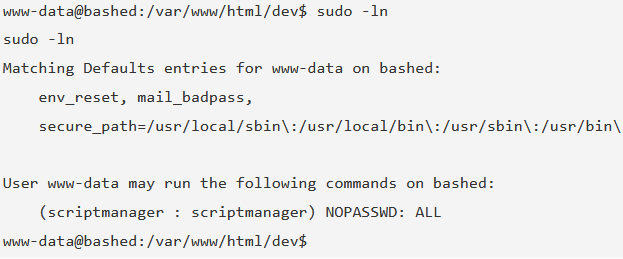
I added a new command to my workflow. This command shows you what commands the current user can run in a sudo context. See an example of HTB Bashed below.
sudo -l
As you can see, this indicates that the user scriptmanager can run commands as sudo without a password. Which brings us to the next thing I’ve learned.
Running bash as another user
With the above functionality, we are able to run /bin/bash as another user like so:
sudo -u scriptmanager /bin/bash
That would change the user from www-data@bashed to scriptmanager@bashed, very handy for privilege escalation.
HTTP Parameter Pollution
I also learned about HTTP Parameter Pollution in the Real-World Bug Hunting book. HTTP Parameter Pollution (HPP) is used to manipulate the parameters a website receives with an HTTP request. The attacker would inject extra parameters into a request the website trusts.
There is Server-Side HPP and Client-Side HPP.
The goal of Server-Side HPP is to send unexpected information to a server and make it return unexpected results.
Client-Side HPP, on the other hand, is used to inject extra parameters into a URL to reflect them on the user’s end. HPP Vulns are quite hard to find and require Thorough testing. Social Media Links are a good place to start looking.
Example Server Side HPP:
You would change
https://www.bank.com/transfer?from=12345&to=67890&amount=5000
to something like
https://www.bank.com/transfer?from=12345&to=67890&amount=5000&from=ABCDEF
You get the idea.
Credit for this example goes to Peter Yaworski and Real-World Bug Hunting.
Compiling and using Exploits written in C
This was always kind of a scary topic for me, as I have never used a manual exploit before. Turns out, it’s not all that hard. When you find an exploit.c file with, for example, Searchsploit, or you just download one from the internet, you need to first compile the exploit.
To do that you can use the Kali included tool gcc:
gcc exploit.c -o exploitCompiled
After that, you can upload the exploit to a server and run it. Quite simple.
Conclusion Week #13
I probably have learned more, but it was a turbulent week for me so I tend to forget stuff. Anyway, I prefer to keep those posts shorter but frequent. I hope you enjoyed it. See you next week.