Nikto is a widely used tool for web vulnerability testing. The tool was developed in the Perl language, and released back in 2011. Security analysts scan for website vulnerabilities with Nikto. However, it will check for many other vulnerabilities, but not all of the results need to be severe, few of them are just for information, not an actual flaw, but still, many of them are real vulnerabilities that are needed to be fixed.
When you scan for website vulnerabilities with Nikto, the tool searches for 6000+ vulnerabilities. This capability makes this tool stand out from other tools on the market. These tests are automatically done after giving the command to Nikto.
Nikto Introduction
Nikto was first developed by Chris Sullo, but now it is under David Lodge’s wings, and other cybersecurity organizations elaborated as well. This tool can easily be installed on any Unix-like system which is capable of running Perl, as this tool is based on the Perl language.
Nikto comes pre-installed in the Kali Linux operating system and in all of its derivations. It is open-source, developers are welcomed to make changes. It also supports host authentication, proxies, IDS evasion, SSL, and many more features.
Nikto is updated once you open it in your CLI of Kali Linux or from any other distro. The tool is widely used by pentesters and hackers to explore many vulnerabilities. It explores the following types of vulnerabilities.
- Files and Programs that are not secure
- Programs and Servers that are outdated
- Server Misconfigurations
- Default programs and files
It looks for almost all kinds of CGIs and files that can be considered malicious to your web server. It can also be used for cookie capturing and printing.
Nikto Installation
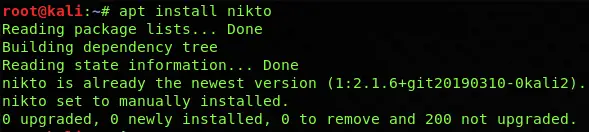
Nikto Installation is pretty easy on all Unix-based systems, it comes pre-installed in Kali Linux, in some cases if it is not present in the Vulnerability Analysis section, then you can manually install it.
To install Nikto, you can simply get it from Nikto’s official GitHub source. You need to simply run the following command to install Nikto.
apt install nikto
Installing Nikto on Ubuntu
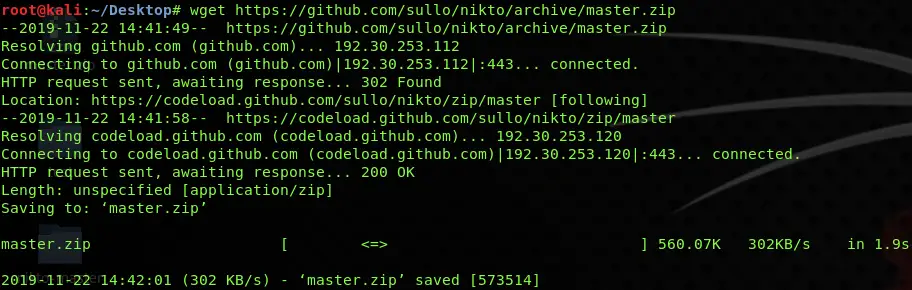
First of all, you have to download all the Nikto sources from their GitHub link by typing a command in Ubuntu’s terminal. Use the following command to do so;
wget https://github.com/sullo/nikto/archive/master.zip
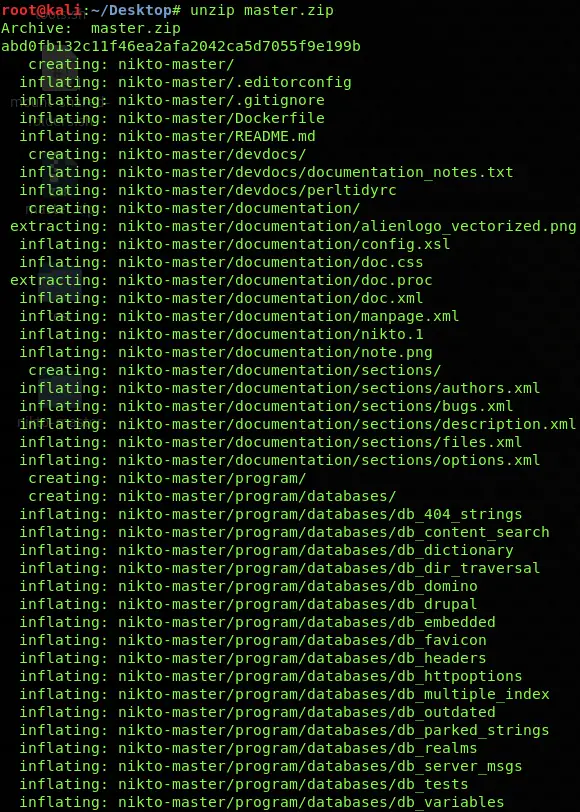
Once you unpacked the file by using any archive manager, then run the following commands to proceed.
unzip master.zip
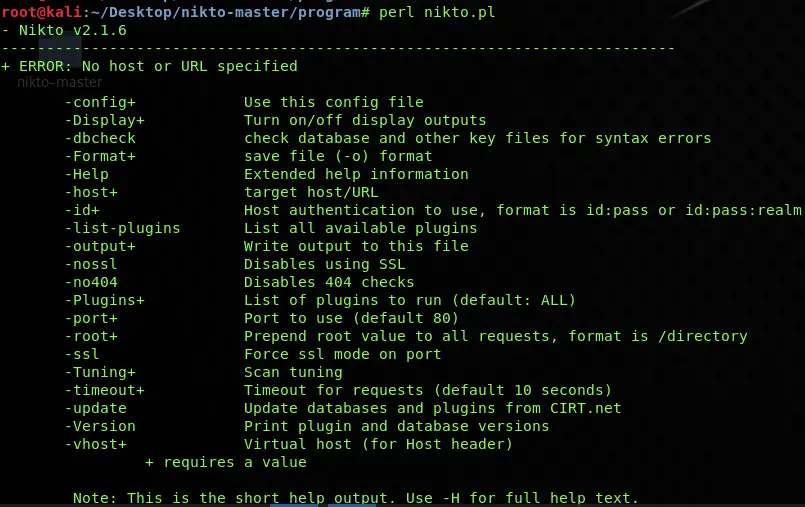
cd nikto-master/program
perl nikto.pl
After running these commands, your Nikto will be successfully installed on your Ubuntu system, and you will an output generated by the Nikto tool.
Start Using Nikto
Once you have installed Nikto correctly and it’s working fine, it’s time to take your first step towards Nikto usage. To get started with Nikto, use the following command, and just have a look at different options that are used within Nikto.
nikto -Help
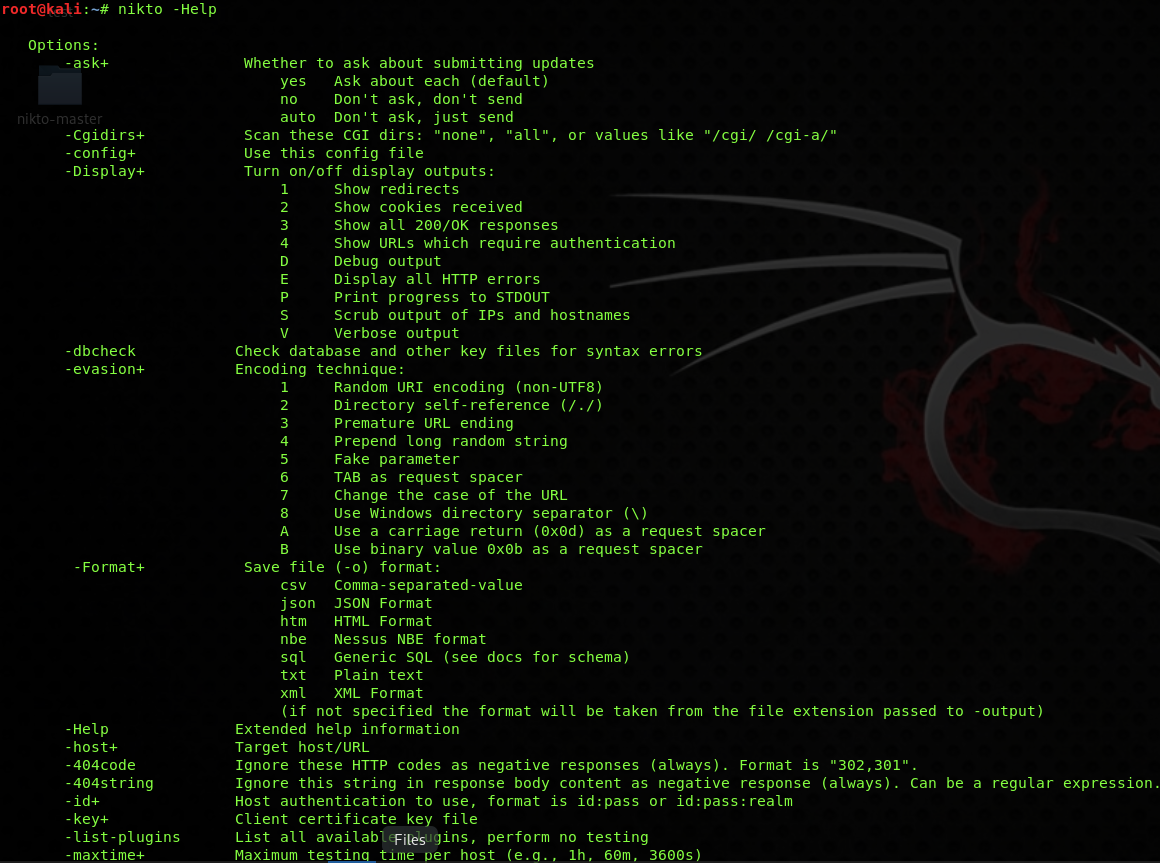
After executing it, you will see the options provided by the tool to perform various types of scans by specifying different switches. You can find all its latest usage options here on their official GitHub source.
Performing Basic Scan
Performing a basic scan through Nikto is pretty easy. Just enter the URL or IP address of the website you want to scan. Let’s take testphp.vulnweb.com as an example. Now to scan a website, you need to use the following syntax:
nikto -h <server-address> -p <port>
In this case, there are two options where:
-h specifies the website or server IP address that you want to scan.
-p specifies the port, mostly it’s 80 by default, but some servers may use a different port.
You should keep in mind that a group of websites may be hosted on the same server, which means that all websites will have the same IP address. So, you should use a hostname instead to specify your target that you want to scan. There will be a different port for the websites that utilize SSL for their security.
In the case of testphp.vulnweb.com, we can simply use the following command to perform a basic scan with basic options.
nikto -h testphp.vulnweb.com -p 80
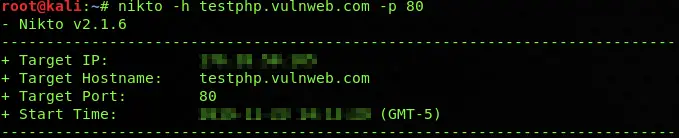
Now, if the website was secured with SSL, then you will probably see the information regarding SSL, and for these secured websites, Nikto will run other vulnerability scans to find any possible flaw present in the system. The scanning process is not always so fast, and it will obviously take some time to complete because Nikto scans it deeply, and for deep scanning, it takes a while to finish.
Once Nikto finishes the scan, you will now see the list of vulnerabilities present in the website and web server. Some vulnerabilities will be just informational, while others could be very critical.
Nikto tells us about many vulnerabilities, issues, and information, including.
- Web-server details
- Installation files for Apache server
- Access to backend files with the help of Directory indexing
- Number of entries in a text file
Hackers can scan for website vulnerabilities with Nikto to use a dedicated exploit in order to hack a website while if an information security analyst would scan for website vulnerabilities with Nikto to find these vulnerabilities, and then he will report it to the website owner to get them fixed so that hackers will not be able to exploit them.
Directory Indexing Flaw
A directory indexing flaw permits anybody visiting the site to get to records that dwell toward the back of the webserver. These might incorporate documents containing code, and in certain cases, even reinforcement records. This is the outcome of poor authorization settings on indexes inside the site. In certain cases, it is conceivable to acquire framework and database association records containing substantial certifications.
Directory indexing can be avoided by setting up suitable authorizations on records and catalogs inside the webserver. Setting up the appropriate permissions helps you to avoid being exploited by a tool like Nikto. It is crucial to set the right permissions on all the files residing on your web servers.
The robots.txt passages that limit web search tools from having the option to get to the four catalogs. It should be noticed that it is not a perpetual arrangement, and document and organizer authorizations ought to be assessed.
Installation files
Default installation records may uncover a ton of data concerning the web server, and this may enable hackers to perform harmful attacks that explicitly focus on the web server according to the revealed data. These files are needed to be hidden correctly, otherwise, they can leak sensitive data related to your website.
Saving scan results
In order to save your scan results before starting your scan, you can use the following form of syntax.
nikto -h <hostname-or-IP> -p <port-number> -output <destination> -format <file-type>
In the above syntax following options are introduced including
-output – To give a path where your results are to be saved, for example, root/Desktop/ABC.
-format – It is used to specify the file type in which form your scan results are to be saved. It could be HTML or TXT.
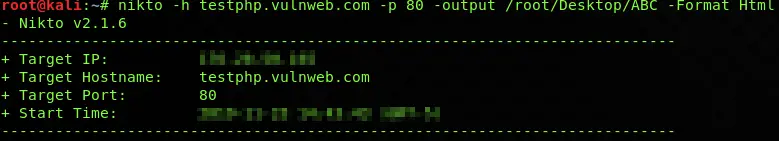
Combining these options for host testphp.vulnweb.com, we can use this command as an example:
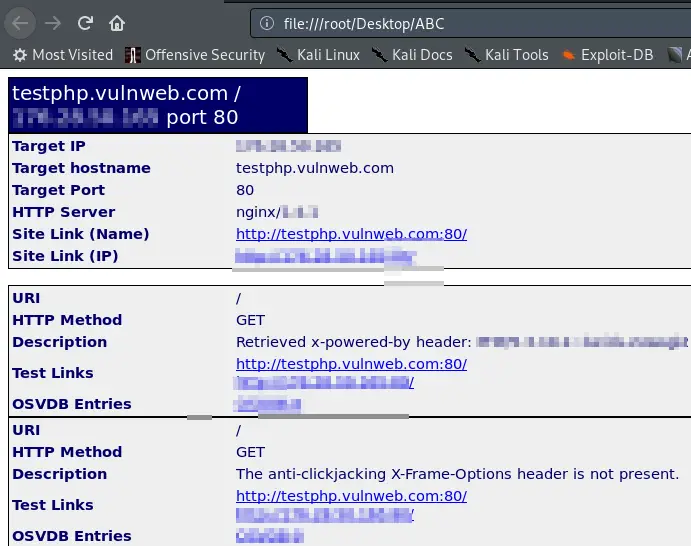
nikto -h testphp.vulnweb.com -p 80 -output /root/Desktop/ABC -Format Html
The scan will normally run after executing this command, but the only difference is that now your scan results will be saved in a beautiful (easy-to-read) form, where you can now check them as many times as you want.
Multiple port testing
You may have tried a single port testing scan using Nikto, but do you know that you can scan more than one port at the same time? It’s pretty simple. You have to use the same
-p switch and put down different ports separated by a comma (,). Now your final command with multiple port testing will look like this.
To scan a website “testphp.vulnweb.com” with two ports that are 80 and 433, we will use -p option and ports will be separated by a comma.
nikto -h testphp.vulnweb.com -p 80,433
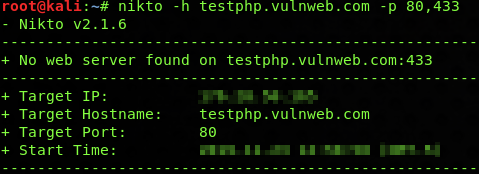
Now when you execute this Nikto command, it will automatically scan for both ports.
Nikto Update
Nikto updates are released regularly to add new features and to improve the Nikto tool. New plugins are added, and databases are improved. Updating Nikto is very simple. Sometimes, it will automatically update when you start it in your Kali Linux terminal. If it doesn’t start updating, then you can do it manually by using -update switch.
Just open Nikto and write the following command with -update switch
nikto -update
Updates will be automatically installed now. Sit back and wait for them to complete.
Scan using tuning option
The tuning option is used to specify which tests are run against the target website. The X option is used to exclude any tests that you do not need. The numbers below represent the different available options to be used with the tuning option.
0 – Used to represent “File Upload.”
1 – Used to represent “Interesting file
2 – Misconfiguration files
3 – For Information Disclosure
4 – HTML/XSS injection
5 – Remote File
6 – DDOS scan
7 – Server Wide – Remote File
8 – Remote execution
9 – SQLI
X – to do the reverse or tuning option
Now, to run a test by using the tuning option, you can simply add the -tuning switch with the number from the above to perform the scan relating to that specific number, for example, to scan for a HTML/XSS injection on a host named as testphp.vulnweb.com, we will use the option -tuning with number 4.
nikto -Tuning 4 -h testphp.vulnweb.com -p 80
![]()
You can also perform multiple tests by using morgen tuning options at once. For example, to perform a test for SQLI and Remote execution vulnerabilities on the website testphp.vulnweb.com, we can use the following command.
nikto -Tuning 89 -h testphp.vulnweb.com -p 80
![]()
Conclusion
There is no doubt that Nikto is the all-time favorite tool for hackers and pentesters as they scan for website vulnerabilities with Nikto. The right tool in the right hands can save your website from any harmful attack, while the same tool can disclose a lot of information that can be used by a hacker to exploit your website.
With over 6700 vulnerability scans, this tool is obviously capable of scanning a website deep down. By learning tool options from their official GitHub, you can get the best possible results from Nikto. It is even listed in our The Best Ethical Hacking Tools in 2019, you can check this article for other favorite hacker tools as well.